Decrypt WEP Traffic using Bruteforce with Insufficient IVs
In this tutorial, you will learn how to crack the WEP key using only one data packet and a wordlist, and then use the wireshark tool to decode the data packet.

Hello World! You might be aware that if you have enough distinct starting vectors, it is simple to crack the WEP key from the network grab. If you are new, don't worry; I will go into more depth on how WEP works and how to break its encryption in later articles.
Think about a scenario where you are able to gather some WEP packets but not enough to crack the key with aircrack-ng and you receive the message "Failed. Next try with \( (X) \) IVs" and due to some conditions you have to go offline to attempt to crack it. In this situation, your options are to create a dictionary and attempt manual decryption. I'll give a Python script in this post that you may use to automate this process.
I have the wordlist and the capture file in my workspace directory. The wordlist is available in the seclists repository, and I downloaded this capture file from AttackDefense lab to use as an example.
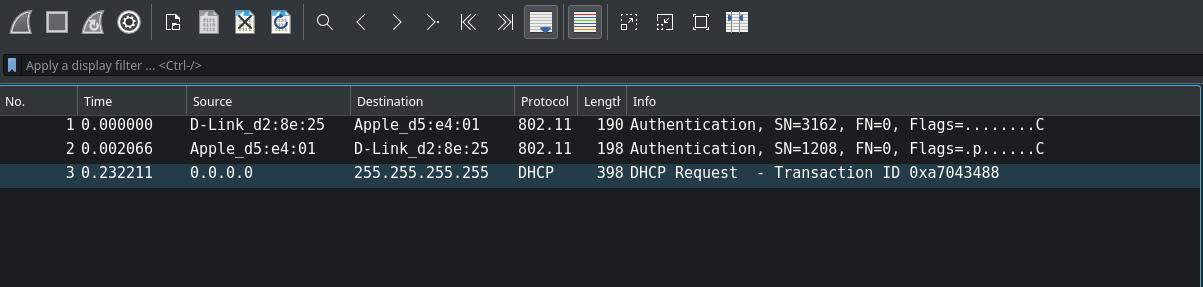
As you can see, there is just one data packet, and wireshark would have understood the protocol if the communication had not been encrypted.
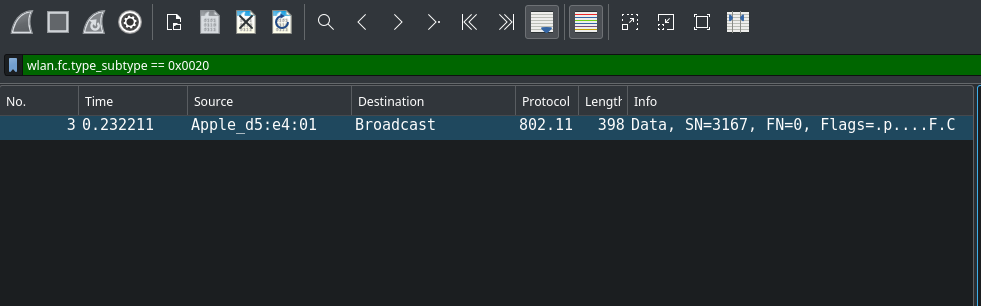
You can tell that the packet contains just one BSSID by looking at the Wireless \( \to \) WLAN Traffic: "00:21:91:D2:8E:25".
Airdecap-ng Usage
Let's first examine the parameters and application of the tool itself before attempting to automate the process. The hexadecimal PSK and the initialization vector's 24 bits are combined to create the WEP encryption key, which has two lengths.
- Breaking \( 64 \) bits encryption key into parts give \( 40 \) bits (or 5 letters ASCII) preshared key and a random \( 24 \) bits of initialization vector.
- Breaking \( 128 \) bits encryption key into parts give \( 104 \) bits (or 13 letters ASCII) preshared key and a random \( 24 \) bits of initialization vector.
So let's try to decrypt the data packet in the wep-traffic.cap file using any five-letter string (in this case, "test1") converted to hex representation. The hexed form of the key, which may be obtained via the xxd tool, and then passed on to airdecap-ng -w parameter as illustrated below.
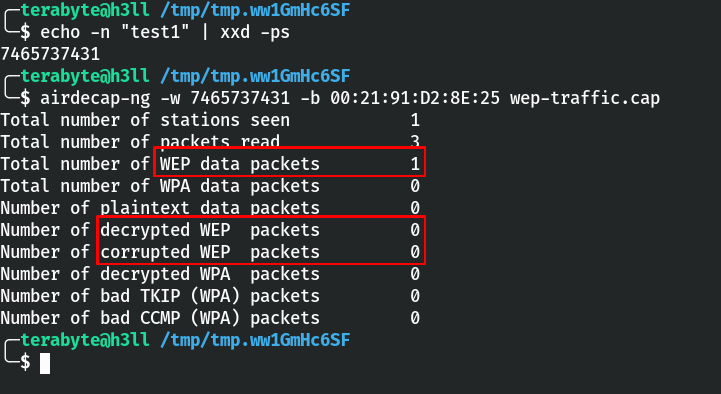
Obviously, test1 is the incorrect key, so this will fail, but at least we know what message it will display. The solution is to repeatedly call airdecap with various keys and compare the resulting output; if there is any difference, we can infer that the cracking process was successful.
Cracking The Code
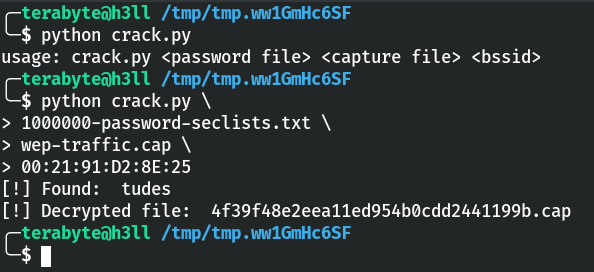
I have included a complete explanation of the code in the wep_decrypt.py file. You can download it to your workspace folder and run the script with 00:21:91:D2:8E:25 as the target BSSID, wep-traffic.cap as the capture file, and 1000000-password-seclists.txt as the wordlist.
python crack.py \
1000000-password-seclists.txt \
wep-traffic.cap \
00:21:91:D2:8E:25You will observe that the tool has successfully decrypted the data packet and the preshared key is "tudes".
Decrypt the Traffic in Wireshark
Of course, you can use the airdecap-ng output to access the decrypted capture file, but what's the fun in that? Let's decrypt the packet using Wireshark by following these procedures.
- Convert tudes to hex using xxd
echo -n "tudes" | xxd -ps # outputs 7475646573 - Open the wireshark provide wep-capture.cap as first argument
wireshark wep-capture.cap & - Open the preferences from Edit menu, or you can press Ctrl + Shift * P keys
- Expand Protocols section and select IEEE 802.11 from the list
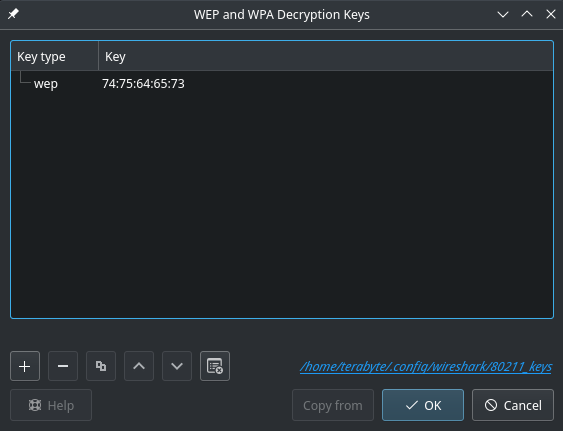
- Click Edit button beside Decryption Keys label, this will open a dialog box with title WEP and WPA Decryption keys
- Click the + button, select "wep" in key type and provide the key "74:75:64:65:73"
Now, click the Ok button, and all of the encrypted data packets will be displayed. As you can see, Wireshark has correctly identified the data packet as a DHCP Request.