Identify the issues in Docker setup using Dockscan
This post will lead you through the process of identifying and assessing vulnerabilities in the Docker service installation.

Hello, world! So far we have seen or will see how to exploit a docker container or secure the docker registry or engine endpoint using various best practices. But what about the docker setup itself? How do you identify problems in your docker installation and setup?
In that case, you can use a tool called Dockscan. It is specifically designed and developed to scan security vulnerabilities and audit the docker installations.
The docker daemon is running in this lab with default settings, as it was during the installation, and can be accessed via the UNIX socket unix:///run/docker.sock file.
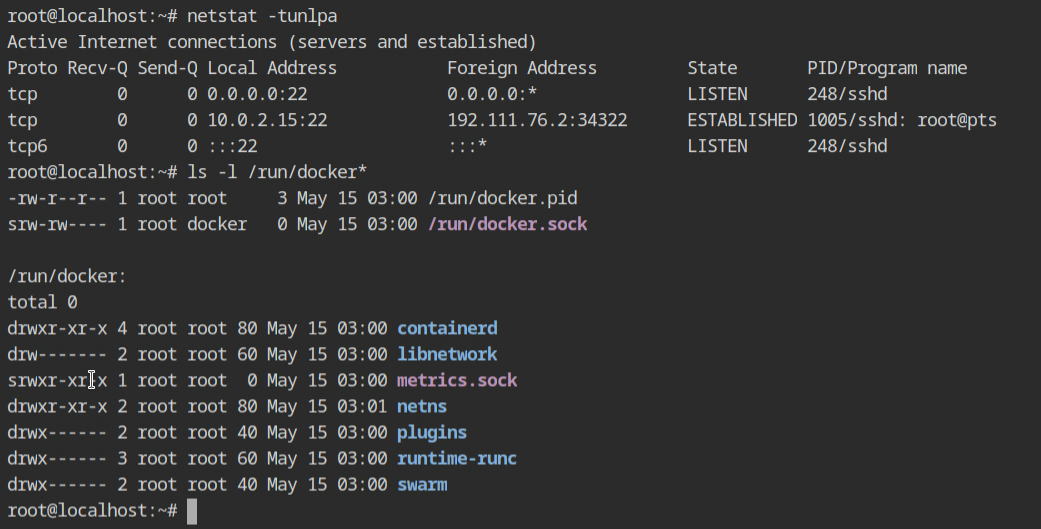
The CLI tool dockscan is also installed and it accepts either tcp:// or unix:// socket to perform the scanning and auditing.
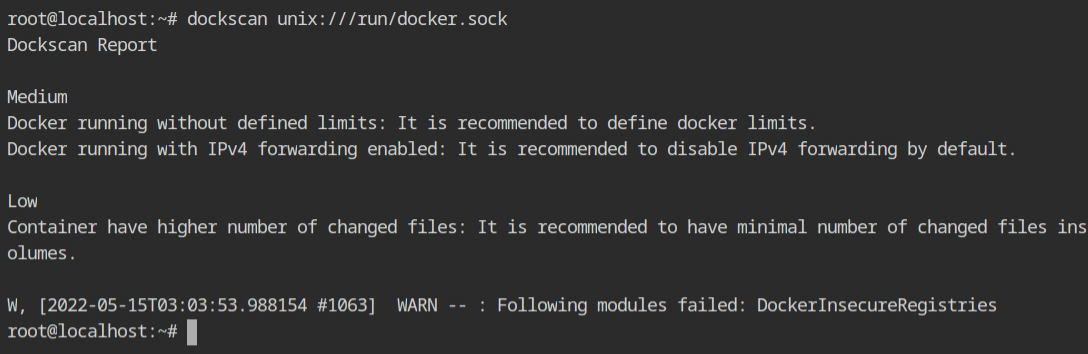
After running the tool on the UNIX socket and performing some background checks, you will receive the following output, which is organised by severity level. Fortunately, no HIGH-level misconfigurations have been reported with the current setup. However, there are some Medium and Low-level findings, and you'll be surprised to learn that it also checks for running container setup misconfigs.
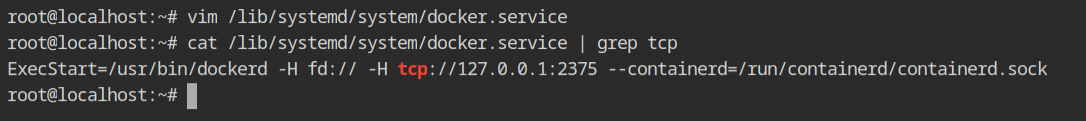
Let's reconfigure the docker systemd service profile to expose the TCP listener for testing with the dockscan tool. You can file the configuration in the /lib/systemd/system/docker.service file.
To enable TCP host, change the ExecStart line and add -H tcp://127.0.0.1:2375 as shown below.
Once these daemon files are changed, it is required to reload them before restarting the services. You can do this by executing systemctl daemon-reload command and then service docker restart to stop and start the docker. You will see that the 2375 port is open on the 127.0.0.1 interface with LISTEN state and the process name is dockerd.
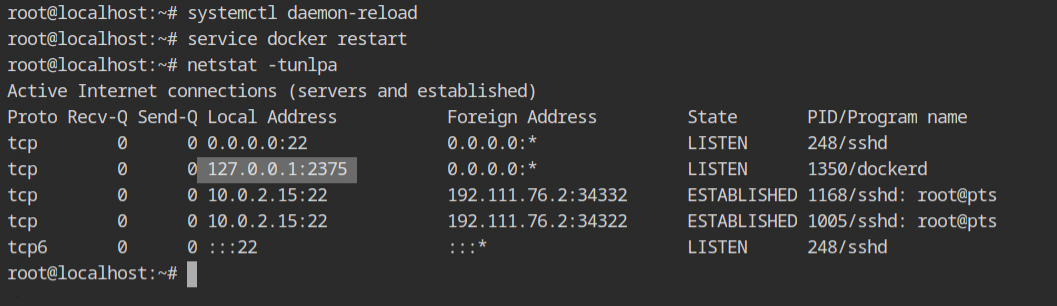
Now, instead of using the UNIX socket, use tcp://127.0.0.1:2375 to run the dockscan tool, and you'll get the following output, with no Low-level error this time. This is because when we restarted the service, it first shut down all the containers before shutting down the Docker daemon. There is no docker container running this time to check for.
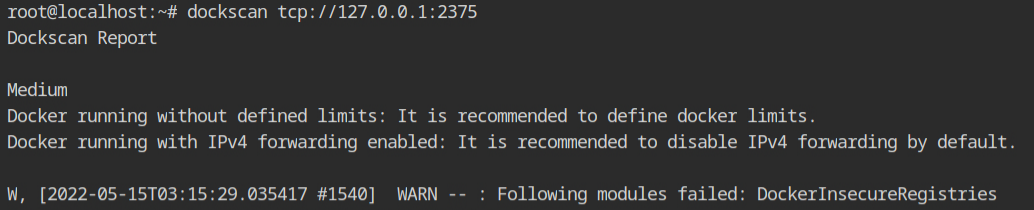
Note – I tried using the following docker config to resolve these issues, but it did not work in my situation. If you find a solution to this problem, please let me know so that I can discuss it here.
{
"containerd": "/run/containerd/containerd.sock",
"ip-forward": false,
"hosts": ["tcp://127.0.0.1:2375"],
"default-ulimits": {
"nofile": {
"Hard": 64000,
"Name": "nofile",
"Soft": 64000
}
}
}/etc/docker/daemon.json fileResources
- https://github.com/kost/dockscan
- https://stackoverflow.com/questions/39473687/how-to-change-dockerd-parameters-with-systemd
- https://unix.stackexchange.com/questions/542343/docker-service-how-to-edit-systemd-service-file
- https://docs.docker.com/engine/reference/commandline/dockerd/#daemon-configuration-file
