Understanding Linux File Permissions
Get in-depth knowledge of Linux file permission from administration and infosec point of you.

In Linux, everything is a file. Even a directory is considered a file containing links to other files (also directories). You can learn about Linux file systems from TLDP's article I will cover this later in restricted environment topic
In this, you will learn about how Linux manages file permissions in a multi-user environment and how you can exploit it to gain the root user shell if it is not set properly.
Since Linux is a multi-user operating system, so it manages 3 set permissions for each file or directory.
- owner
- group
- others
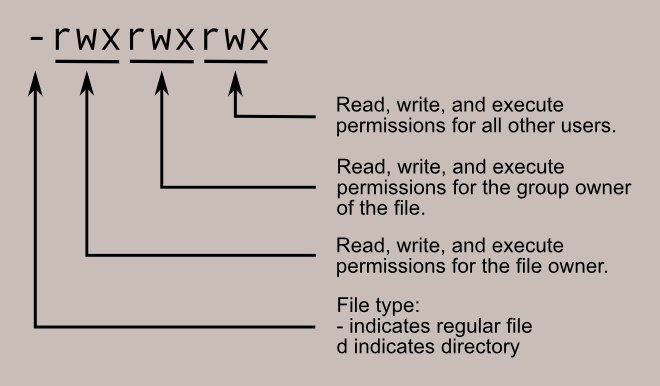
drwxr-xr-x 2 terabyte terabyte 40 Aug 5 00:02 dir
-rwxr-xr-x 1 terabyte terabyte 7 Aug 5 00:01 fileLet's focus on the first 10 characters. The very first character tells about file type, d means directory and - means normal file
After this, you will see repeating rwx for 3 times. The meaning of each character is as follows
- r – read permission on the file
- w – write permission on the file
- x – executable permission on the file
After permissions, you will see two words terabyte and again terabyte. In this pair, the first one tells you the owner to whom this file belongs and the latter one tells the group of the file.
Now where this information is stored? For users, you can file this information in /etc/passwd file and for groups it is /etc/group
Why do you need to have a group in a multi-user operating system anyway? Think of a situation, you want to give certain permission to some users on a particular file but the owner of that file is not willing to share his/her credentials as the home directory of that user contain some private stuff. So in this case, to keep everyone happy the root user will set file permission in such a way that the group of users can access it from their login without switching it to the target user.
To add a group to a user, you need to run usermod -aG <group name> <login name> the command from the root user. This is because it will update /etc/group file which is only writable by the root user
$ ls /etc/group -l
-rw-r--r-- 1 root root 1156 Jul 27 11:40 /etc/groupHow Linux Match Password and Perform Login
If you will check the content of /etc/passwd file focus on the non-service account with a valid shell to log in. For example, all the entries ending with /usr/bin/nologin is considered as the service account
You can use the following command to get a list of all the login accounts
$ cat /etc/passwd | grep -E 'sh$'Which will be in the following format
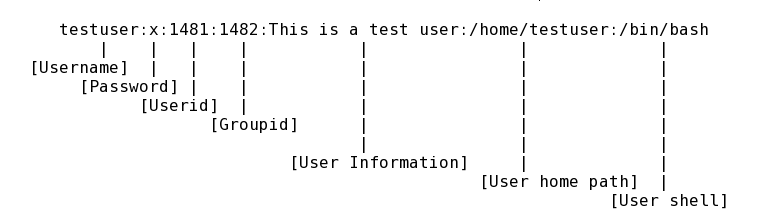
You see the second part is x. This means that password of the user can be found in the /etc/shadow file. Similarly, for groups, the password file is /etc/gshadow. These shadow files are only accessible to the root user. Unlike the passwd file, you can't even see the content of /etc/shadow
$ cat /etc/shadow
cat: /etc/shadow: Permission deniedThe format of the shadow file is similar to the passwd file but each part has a different meaning except the first one
mark:$6$.n.:17736:0:99999:7:::
[--] [----] [---] - [---] ----
| | | | | |||+-----------> 9. Unused
| | | | | ||+------------> 8. Expiration date
| | | | | |+-------------> 7. Inactivity period
| | | | | +--------------> 6. Warning period
| | | | +------------------> 5. Maximum password age
| | | +----------------------> 4. Minimum password age
| | +--------------------------> 3. Last password change
| +---------------------------------> 2. Encrypted Password
+----------------------------------------> 1. UsernameSome services (like FTP, ssh) require checking the existence of a username in the system and performing authentication steps. So if the passwd file will have a list of all the passwords, anyone could read and crack the password for the user and eventually gain a foothold on behalf of that user. Hence, Linux introduced a shadow file to keep the password database separate and only rw to the root user to avoid this issue.
You can use the passwd command to update the password of the current user
There are three possible values in 2nd part
- star (*) – means no password set, hence account switch is impossible
- exclamation (!) – means the account is locked
- password hash – a password has information of the type of hash and optional salt value
The format for password could be any of the following
$type_of_hash$encrypted_password
$type_of_hash$plain_text_salt$encrypted_passwordYou can create both of the strings using the OpenSSL utility
$ openssl passwd -1 "hello world"
$1$Y3FAzTxG$/I/sykzmytIduJwbL4mjo1
$ openssl passwd -1 -salt "my salt" "hello world"
$1$my salt$lY65QUBqL1JO3LEh3ENqe.Here. -1 means to use an MD5 hashing algorithm. Get more information about types of hash supported by executing openssl passwd -help
Permissions vs Ownership
While learning about permissions, people often mix this up with the ownership. Permission means, who can perform what actions on a file and ownership tells who owns the file.
If you think both of these are inter-related. As the first two sets in the permission set are for owners and groups.
$ touch file-1
$ su root -c "touch file-2"
Password:
$ ls -l
total 0
-rw-r--r-- 1 terabyte terabyte 0 Aug 5 10:21 file-1
-rw-r--r-- 1 root root 0 Aug 5 10:21 file-2While creating a file, the owner and group are automatically assigned to the file are inherited from the currently logged in users. For example, if I create a file by the root user it will have owner group as root root
Using read permission on a file. The cat operation in Linux will read the content of the file and print it on stdout stream
$ ls -l
total 4
drwxr-xr-x 2 terabyte terabyte 40 Aug 5 00:09 dir
-rwxr-xr-x 1 terabyte terabyte 7 Aug 5 00:01 file
$ cat file
secretIt's not like that once you have created the file and its permissions and ownership will be retained like this forever. Linux is your friend, not your foe. It provides you two utilities: chmod and chown to change the permissions and ownership of a file respectively.
Using these two with non-privileged users makes no sense because due to lack of permissions you will not be able to change read or change the file. The root user is the upmost privileged user in Linux and using that user can do literally anything on the system.
So in this, I will switch to root and change the ownership of file-2 to the user and group terabyte and permissions rwxrwx---
$ ls -l
total 0
-rw-r--r-- 1 terabyte terabyte 0 Aug 5 10:21 file-1
-rw-r--r-- 1 root root 0 Aug 5 10:21 file-2
$ su root -c "chown terabyte:terabyte file-2"
Password:
$ chmod u+rwx,g+rwx,o-rwx file-2
$ ls -l
total 0
-rw-r--r-- 1 terabyte terabyte 0 Aug 5 10:21 file-1
-rwxrwx--- 1 terabyte terabyte 0 Aug 5 10:21 file-2To know more about chmod and chown, I would recommend you first read the man pages.
File Permission vs Directory Permission
Now you will be thinking rwx makes sense for a file, like you want to read/write/execute operations on a file, and in the directory, you want to read files and create files so it requires read and write permission, but why to execute. For directories, execute permission allows you to enter the directory (i.e., cd into it), and to access any of its files.
So if I have a directory without executable permissions, the cd and ls commands will fail like following
$ pwd
/tmp/tests
$ mkdir dir
$ ls -l
total 0
drwxr-xr-x 2 terabyte terabyte 40 Aug 5 10:41 dir
$ chmod -x dir/
$ ls -l
total 0
drw-r--r-- 2 terabyte terabyte 40 Aug 5 10:41 dir
$ cd dir/
sh: cd: dir/: Permission denied
$ ls -la dir/
ls: cannot access 'dir/.': Permission denied
ls: cannot access 'dir/..': Permission denied
total 0
d????????? ? ? ? ? ? .
d????????? ? ? ? ? ? ..Now, if I set the executable permissions on the directory, the above commands will work
$ chmod +x dir/
$ ls -l
total 0
drwxr-xr-x 2 terabyte terabyte 40 Aug 5 10:41 dir
$ pwd
/tmp/tests
$ cd dir/
$ pwd
/tmp/tests/dir
$ ls -la
total 0
drwxr-xr-x 2 terabyte terabyte 40 Aug 5 10:41 .
drwxr-xr-x 3 terabyte terabyte 60 Aug 5 10:41 ..A file first inherits its permission from the directory so for example, if you have a file owned by the root user in the directory which is owned by some other user, let's say it is a terabyte. If you are logged in as a terabyte user, you can still delete that file.
$ ls
dir file supersecret
$ ls -l
total 4
drwxr-xr-x 2 terabyte terabyte 40 Aug 5 00:09 dir
-rwxr-xr-x 1 terabyte terabyte 7 Aug 5 00:01 file
-rw-r--r-- 1 root root 0 Aug 5 10:14 supersecret
$ rm supersecret
rm: remove write-protected regular empty file 'supersecret'? y
$ ls -l
total 4
drwxr-xr-x 2 terabyte terabyte 40 Aug 5 00:09 dir
-rwxr-xr-x 1 terabyte terabyte 7 Aug 5 00:01 fileYou can suppress this warning by calling the rm command with -f flag. This will perform all the actions forcefully when permitted
To practice Linux permissions, I would recommend you try the following labs
In the next post, I will discuss what are the misconfigurations with file permissions and how you can exploit them to gain root user privileged shell. Here you can refer to a cheat sheet for quick reference – https://www.pcwdld.com/linux-commands-cheat-sheet#wbounce-modal
