Wifi Traffic Analysis in Wireshark
In this post, you will learn how to analyse wifi traffic from a large packet capture file and drill down to the information that makes sense.

Hello World! Let's say you have a capture file of the WiFi traffic and you are supposed to contruct some meaning or storyline from it to summarize the attack in your organization. What you will do? The answer is that you will filter the packets and then analyse them, because reading from unfiltered packets doesn't seem to make any sense.
Today I will discuss how to filter the captured packets using "Display Filters" in question and answers format. If you don't have a deep knowledge of concepts I will using following, then don't worry I will write content in the future.
The labs I have been used for the demonstration can be found on the AttackDefense platform
- https://attackdefense.com/challengedetails?cid=1141
- https://attackdefense.com/challengedetails?cid=1143
- https://attackdefense.com/challengedetails?cid=1142
Q1 What is the name of the Open (No Security) SSID present in the packet dump?
Your WiFi access point broadcasts the beacon frame in the air medium after a specific interval of time which can be configured in the settings page as well. This is a subtype management frame which contains the information about the WiFi and instructions to establish connection with it.
The type of management frame type is 0x0 and subtype of the beacon frame is 0x8, in the wireshark you can use the wlan.fc.type_subtype filter variable for this. To display all the beacon frames, you can use wlan.fc.type == 0x0 && wlan.fc.type_subtype == 0x8 filter.
If the WiFI access point is OPEN and no encryption or authentication is enabled, it will have privacy bit in the capabilities flag unset. This information is carried in the Fixed Parameters Set of each beacon frame. To display only open networks, you can use wlan.fixed.capabilities.privacy == 0 filter.
Here is the combined filter I have used in the Wireshark
wlan.fc.type == 0x0 && wlan.fc.type_subtype == 0x8 && wlan.fixed.capabilities.privacy == 0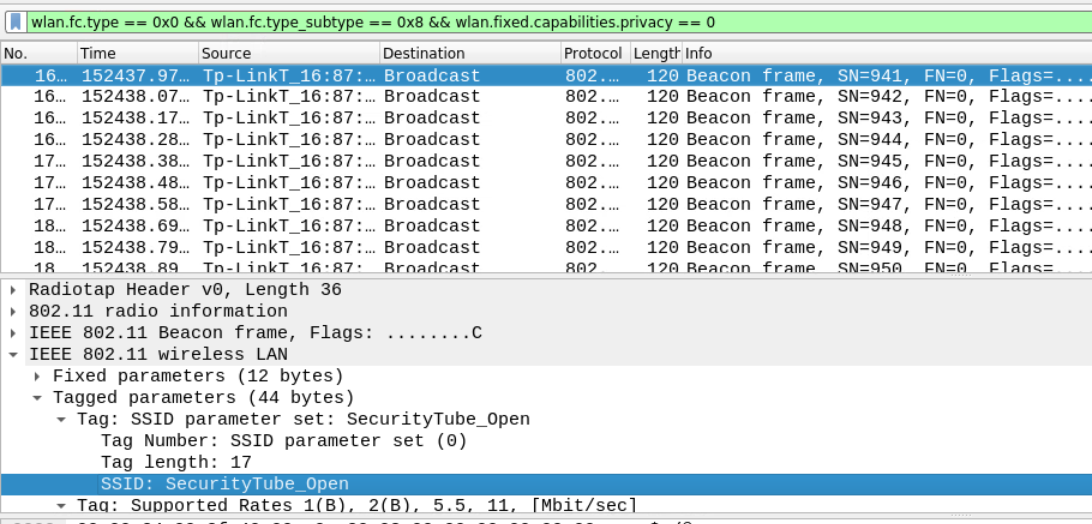
Answer – SecurityTube_Open
Q2 The SSID 'Home_Network' is operating on which channel?
Channels are used to divide the WiFi band into multiple sections to share the same band without causing any interference. If the access point sends beacons in a specific channel, only stations configured in that channel will be aware of the access point's existence. This information is linked with frequency and physical medium, therefore you can find it in the Radio Information section.
The Radio Information section is provided in all the wireless packets therefore you are supposed to filter only the SSID of the access point.
wlan.ssid == "Home_Network"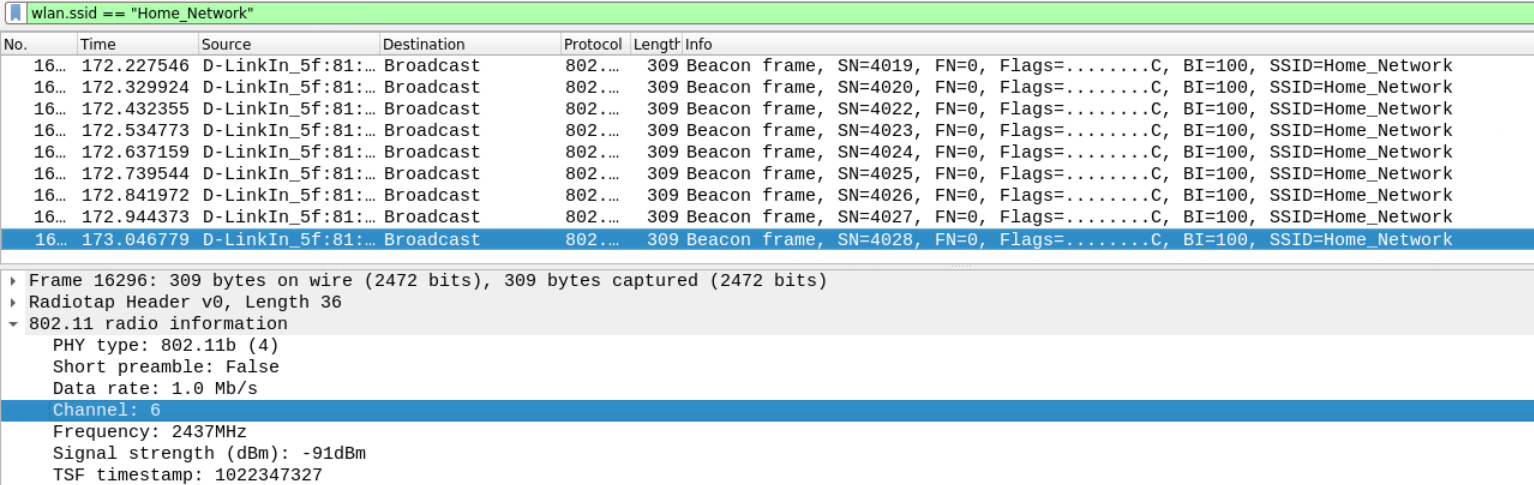
Answer – 6
Q3 Which security mechanism is configured for SSID 'LazyArtists'? Your options are: OPEN, WPA-PSK, WPA2-PSK.
In the beacon frame of the LazyArtists SSID, the RSN tagged parameter is set and we see the authentication mode is PSK (Pre-Shared Key) which means the access point is located in a home or some small office network, but this doesn't reveal the excryption mechanism – is it WPA or WPA2?
If you will check the both Group Cipher Suite and Pairwise Cipher Suite (because cipher is a term in cryptography) you will see that both of them are using AES encryption. Since WPA uses TKIP encryption, and WPA2 is the newer version of the WPA which uses AES encryption, therefore we can conclude that the encryption type is WPA2 here.
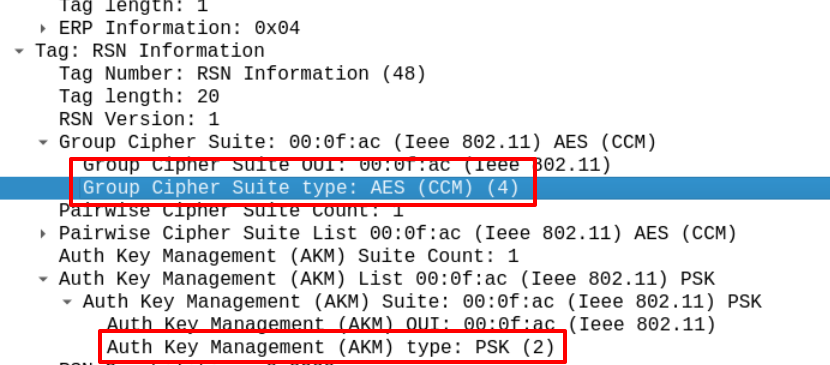
Answer – WPA2-PSK
Q4 Is WiFi Protected Setup (WPS) enabled on SSID 'Amazon Wood'? State Yes or No.
== operator to filter the SSID in wireshark, it will not show any packets because it is performing strict equality. The SSID name in the pcap file has a trailing whitespace. Therefore, you are supposed to use wlan.ssid contains "Amazon Wood" filter.While connecting your printer to WiFi, you may have come across this feature in your WiFi router where you press a WPS button and it will connect your printer to WiFi. Because devices such as printers, kiosks, and IoT devices do not always have keyboards to enter long passwords, WPS allows users to add devices to their Wi-Fi networks in seconds by skipping the password authentication that is normally required.
This feature may differ from one vendor to the next and from one product to the next and the information can be found in the tagged parameter of type 221 (Vendor Specific) with type set to 0x04. WPS functionality is supported by any packet containing this information.
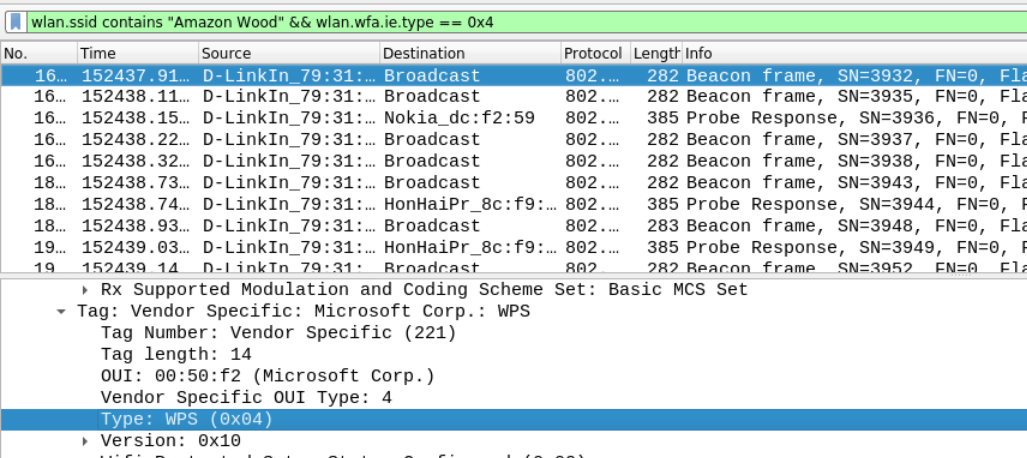
Answer – Yes
Q5 What is the total count of packets which were either transmitted or received by the device with MAC e8:de:27:16:87:18?
The transmitter address (wlan.ta) contains the MAC address of the device from which the wireless frames are sent, and the receiver address (wlan.ra) contains the MAC address of the device where the packets are supposed to be received.
Do not mix up this with the source (wlan.sa) and destination (wlan.da) addresses; these four addresses have different meanings when WDS (Wireless Distribution System), a type of signal extender, is in use.
The display filter you can use in this case (without quoting the MAC address value) is
wlan.ta == e8:de:27:16:87:18 || wlan.ra == e8:de:27:16:87:18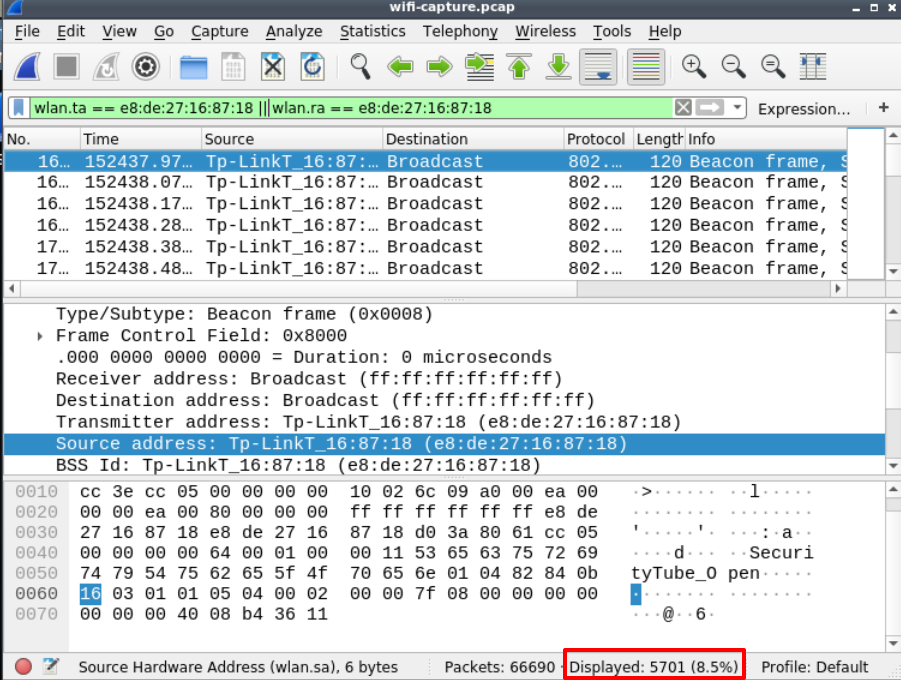
Answer – 5701
Q6 What is the MAC address of the station which exchanged data packets with SSID 'SecurityTube_Open'?
The SSID field only exists in either Beacon Frame, Probe Request or Probe Response and these frames doesn't contain any "data". Since SecurityType_Open is a access point, it's BSSID will always contain the MAC address of the device. You can get the wlan.bssid for the wlan.ssid == "SecurityType_Open" SSID. For simplicity, I have used the Tshark in this case, but you can also do this in the wireshark as well.
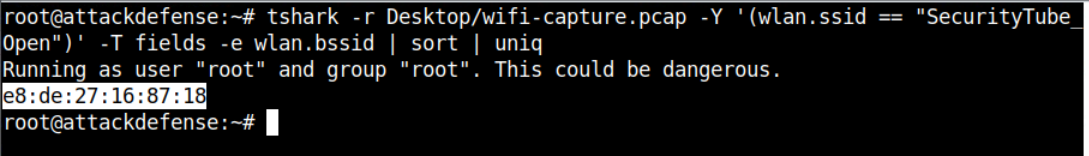
To get the value of the type_subtype field, you need concat the binary value in format type:subtype which can then be converted into hexadecimal format from the python as shown below.
hex(0b100000) # 0x20, data packetIf the station is sending any data to the access point, it must set the BSSID in the wlan.ra field and must have the frame control type_subtype set to 0x20. As a result, you can use the following display filter to get a list of all data packets sent from the station to the access point.
wlan.fc.type_subtype == 0x20 && wlan.ra == e8:de:27:16:87:18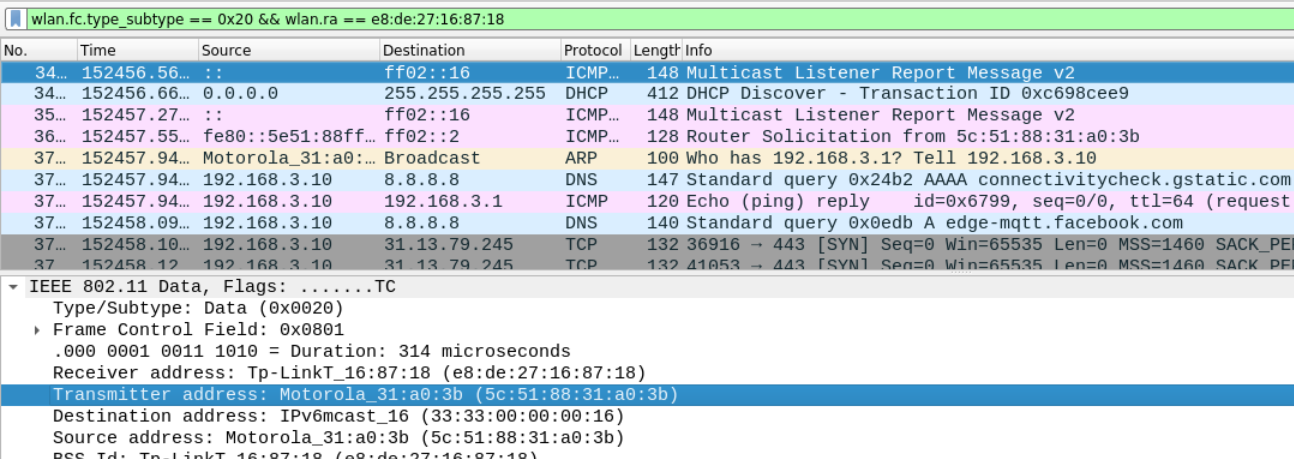
Answer – 5c:51:88:31:a0:3b
Q7 From the last question, we know that a station was connected to SSID 'SecurityTube_Open'. Provide TSF timestamp of the association response sent from the access point to this station.
TSF timestamp is used to synchronize the stations in a BSS and is located in the Radio Information section. The subtype of the association response frame from management type is 0x1 and it always originated from the access point for the station. Therefore you can use the MAC of the client from previous question in the wlan.ra.
wlan.ta == e8:de:27:16:87:18 && wlan.ra == 5c:51:88:31:a0:3b && wlan.fc.type_subtype == 0x1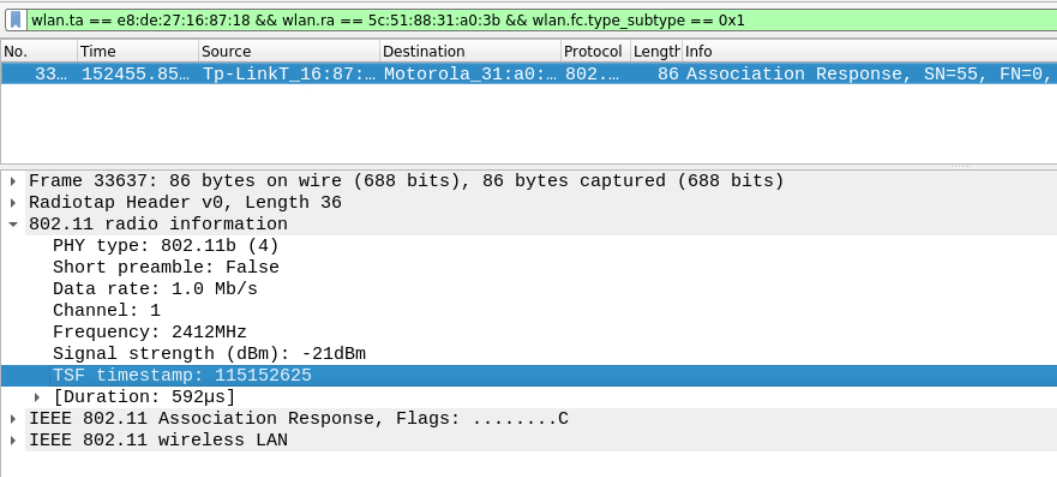
Answer – 115152625
Q8 The BSSID 00:0d:67:3d:4a:49 is operating in which country? Provide the standard two character country code e.g. US, UK.
Country information reveals a lot of information about the WiFi transmission and the most important one is the band and channel it supports. It is defined in all the access points and also broadcasted in all the beacons. You can find this in the Country Information tagged parameter.
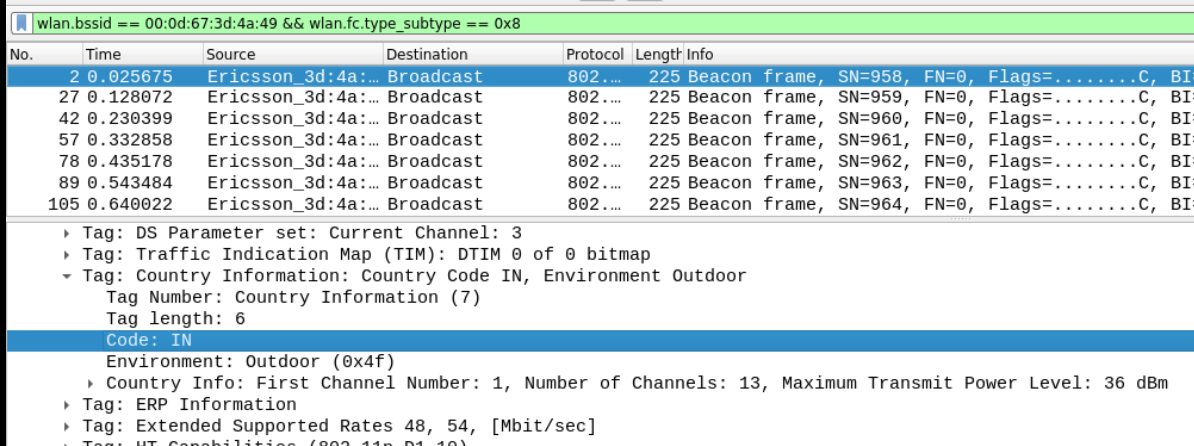
Answer – IN (India)
Q9 How many clients tried to connect with SSID ‘Ruther_SSID’? Consider all connection attempts and not only the successful connections.
When the station attempts to connect to the access point, it sends the association request and waits for the access point's response. This is a subtype of management with the value 0x0. To display all traffic attempting to connect to the Ruther_SSID access point, use the following filter.
wlan.ssid == "Ruther_SSID" && wlan.fc.type_subtype == 0x0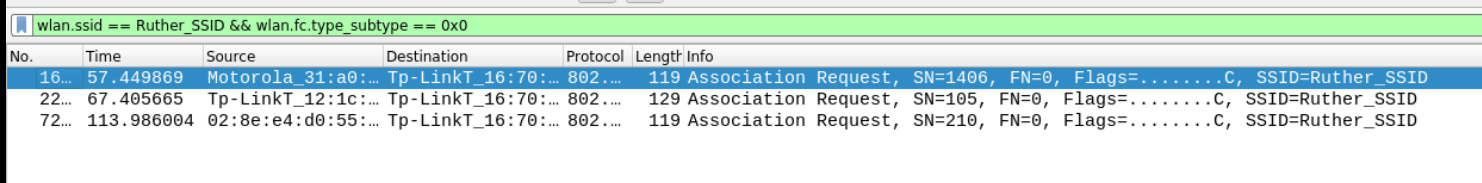
Answer – 3
Q10 Is it possible to launch a passphrase cracking attack on SSID ‘Amazon’? State Yes or No.
The authentication on the LAN (or WLAN here) is done by the EAPOL (Extensible Authentication Protocol over LAN) protocol. Since we have both the authentication information from AP to Station and Station to AP. The filter I have used is
wlan.bssid == 3c:1e:04:2a:08:4f && eapolThis will look for all the traffic with BSSID of the Amazon SSID and eapol information. There are enough handshakes and information exists for launching a successful passphrase attack.
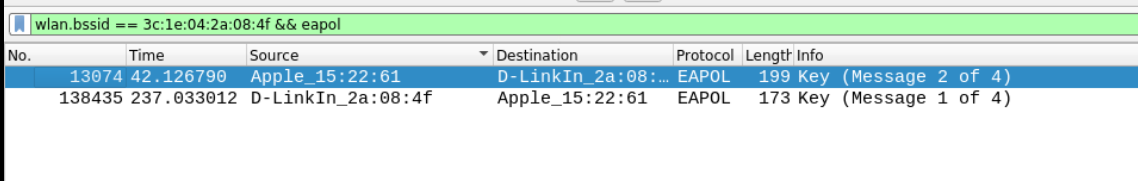
Answer – Yes
Q11 What is the name of the SSID which is using WPA/WPA2-Enterprise security scheme?
As you know by now the difference between WPA and WPA2 is just the encryption algorithm they use. For recap, WPA uses TKIP and WPA2 uses AES encryption. This information can be found in the RSN IE tagged section of the beacon frame with AKMS type set to 0x1.
wlan.fc.type_subtype == 0x08 && wlan.rsn.akms.type == 1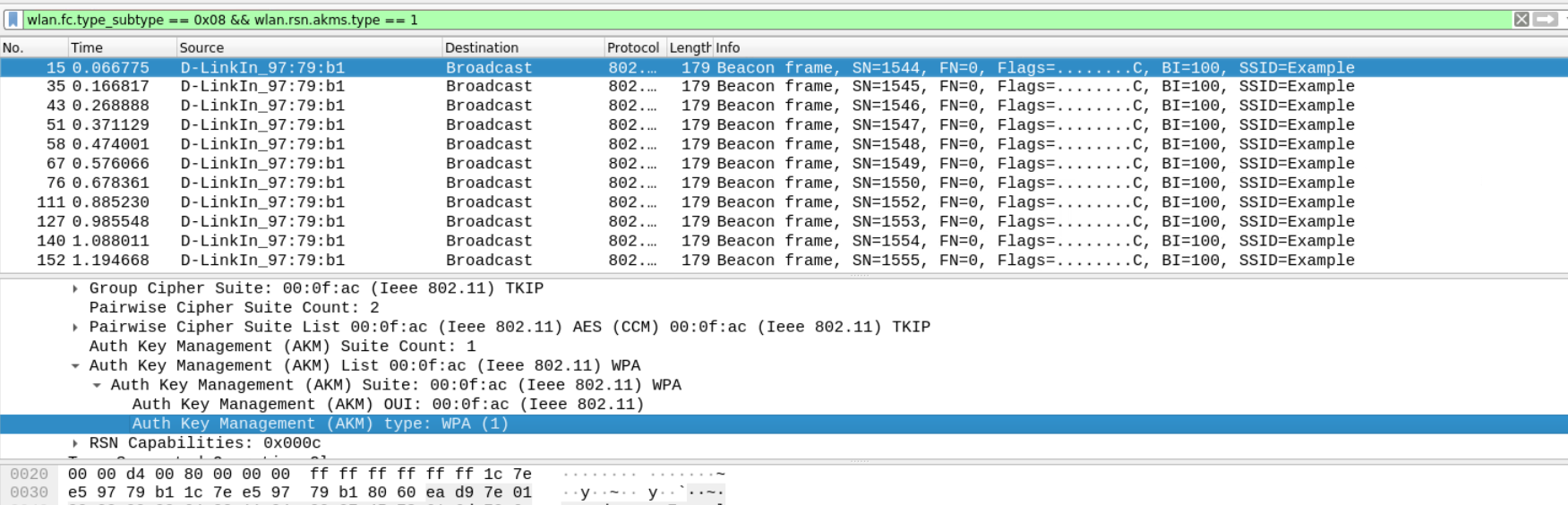
Answer – Example
Q12 A device tried to connect to the SSID mentioned in Q1. What is the MAC address of that device?
The station always send association request to the access point in the starting of the association and authentication. You can filter all the Association Requests and look for the source address in them.
wlan.fc.type_subtype == 0x0 && wlan.ssid == "Example"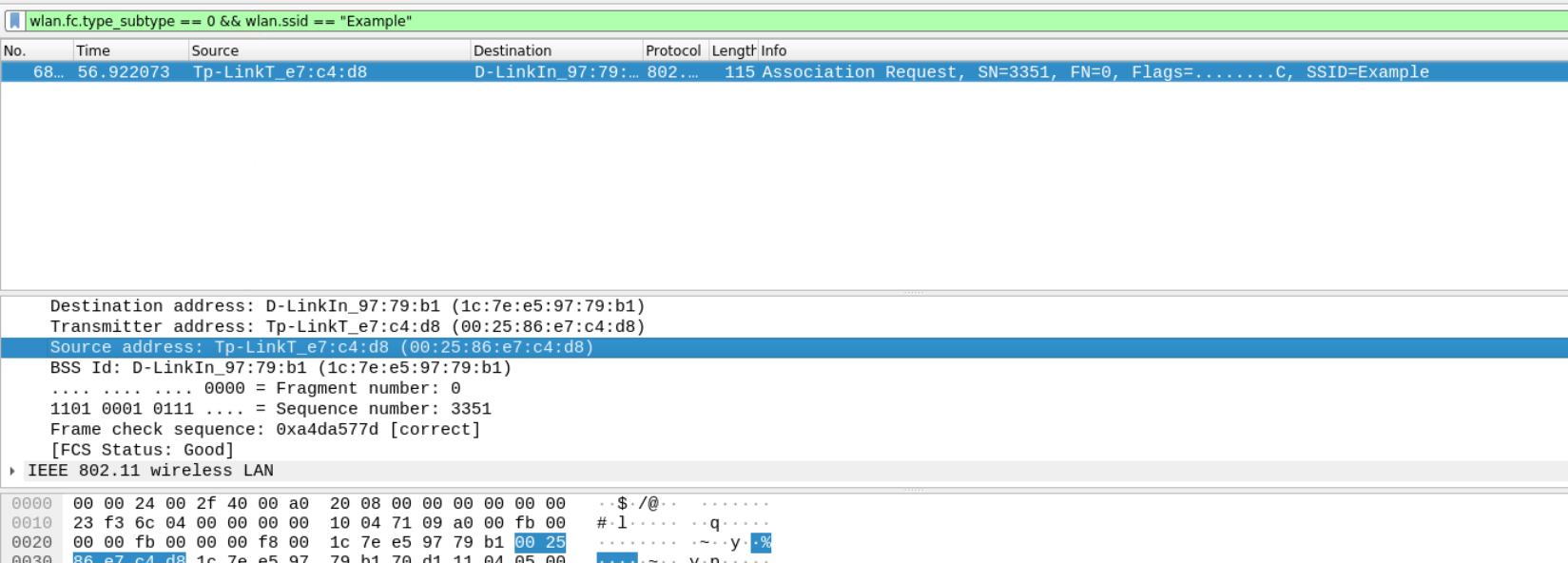
Answer – 00:25:86:e7:c4:d8
Q13 A device tried to connect to the SSID mentioned in Q1. Was the connection attempt successful? State Yes or No.
When the access point receives the association request, it returns the association response to the station, after you use the following filter, you will realize that the access point is not responding. Therefore we can conclude that the connection attempt is unsuccessful.
(wlan.fc.type_subtype == 0x0 || wlan.fc.type_subtype == 0x1 || wlan.fc.type_subtype == 0xb) && wlan.ssid == "Example"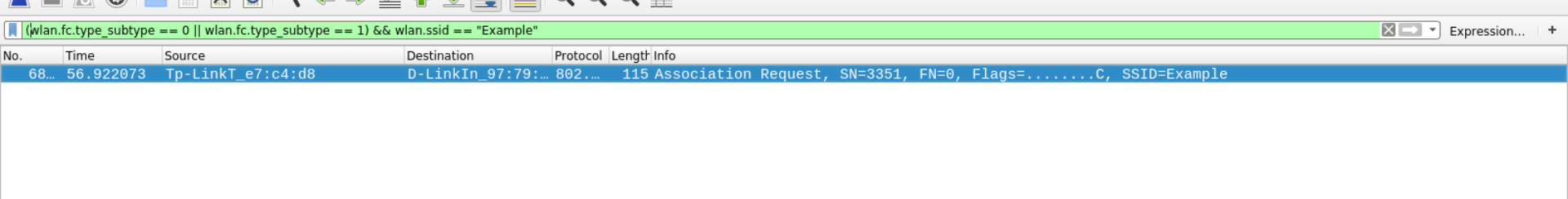
Answer – No
Q14 What kind of EAP (Extended Authentication Protocol) is used by the SSID? Provide answer in form of abbreviation.
EAP is used on encrypted networks to provide a secure way to send identifying information to provide network authentication. It supports various authentication types in which you can neglect eap.type == 0x1.
wlan.ta == 1c:7e:e5:97:79:b1 && eap && !(eap.type == 0x1)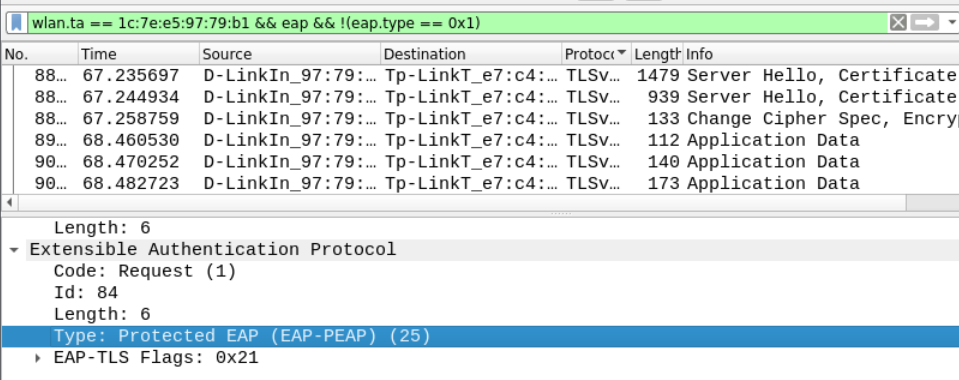
Answe – PEAP
Q15 A deauthentication broadcast message was transmitted by the BSSID 1c:7e:e5:97:79:b1. Provide the time in UTC in DD/MM/YYYY HH:MM:SS format.
A deauthentication message is a notification to an access point from a station or vice versa. This will automatically result in deassociation. Typically, neither party can refuse this, and it is also known as the most noisy attack. It is a part of the management frame and with subtype set to 0xc. To get the answer of this question, you can use following filter and look for the Arrival Time in the Frame section of the disected packet
wlan.sa == 1c:7e:e5:97:79:b1 && wlan.fc.type_subtype == 0xc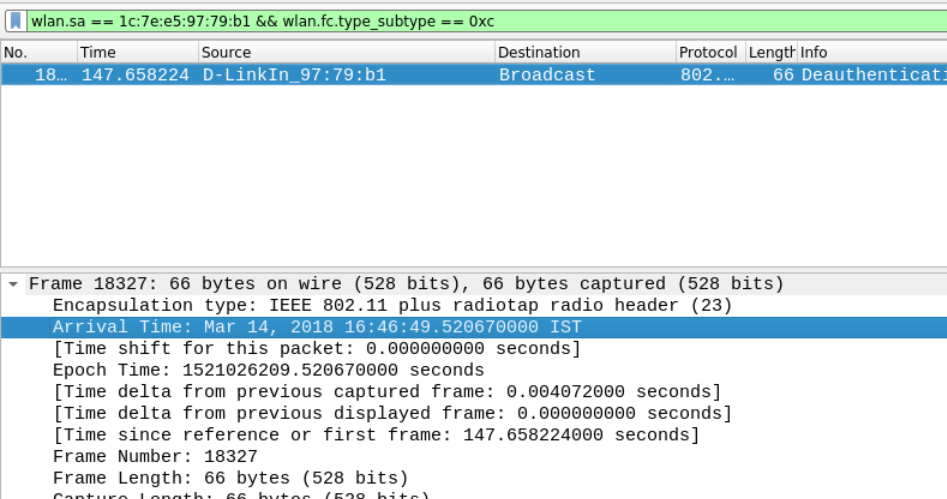
This time is in the IST timezone, to convert it to UTC, subtract 5:30 hours from the time.
Answer – 14/03/2018 12:16:49
Resources
- https://mrncciew.com/2014/08/21/cwsp-rsn-information-elements/
- https://howiwifi.com/2020/07/13/802-11-frame-types-and-formats/
- https://en.wikipedia.org/wiki/802.11_Frame_Types#Types_and_SubTypes
- https://serverfault.com/questions/523294/wireshark-difference-between-fixed-parameters-and-tagged-parameters
- https://stackoverflow.com/questions/46328606/how-to-see-what-encryption-type-a-wlan-uses-in-wireshark
- https://www.avast.com/c-wep-vs-wpa-or-wpa2#topic-4
- https://www.digitalcitizen.life/simple-questions-what-wps-wi-fi-protected-setup/
- https://mrncciew.com/2014/09/28/cwap-mac-headeraddresses/
- https://osqa-ask.wireshark.org/questions/37706/whats-the-difference-between-receiver-address-and-destination-address/
- https://en.wikipedia.org/wiki/Timing_synchronization_function
- https://libertyshield.kayako.com/article/15-change-country-on-vpn-router
- https://mrncciew.com/2014/10/08/802-11-mgmt-beacon-frame
- https://www.mist.com/documentation/what-is-the-difference-between-ap-deauthentication-and-client-deauthentication/
- https://www.techtarget.com/searchsecurity/definition/Extensible-Authentication-Protocol-EAP
- https://www.intel.in/content/www/in/en/support/articles/000006999/wireless/legacy-intel-wireless-products.html
