Brute forcing Password with Hashcat Mask Method
Take a step further in hashcat bruteforcing and learn how to perform a mask attack on the password length when provided the minimum and maximum length and charset of the passwords

In my previous post on hashcat introduction, we have discussed what are hash and how they are created. Also, we have seen that hashes are the irreversible transformation of the data and can only be cracked by launching a brute-force attack or dictionary attack to be precise.
People are getting smarter day by day and it's becoming hard to guess the password or perform dictionary attacks because of so many random password generator services. But the web service provides some information about the minimum or sometimes maximum length of the password which makes an interesting fact as people prefer to choose the minimum length to remember the random password.
In this post, we will first revise the Bruteforce technique using a dictionary and then later move onto the hashcat feature on mask brute-forcing. You can find this lab on attack defence – https://attackdefense.com/challengedetails?cid=61 and I would recommend you to first try out this lab on your own.
Lab Walkthrough
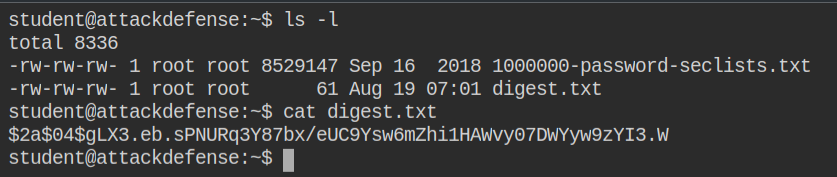
In this lab, I found a digest.txt file containing the hash digest and the number of rounds used for creating it. The digest is the serialized text created from the output of the hash function to store it in a file or database and several rounds mean cost factor: greater the cost factor is, harder it is to brute force. Read more about bcrypt cost factor – https://stackoverflow.com/a/46713082/10362396
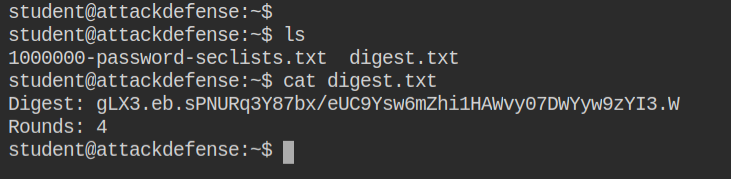
The cost factor is counted as hash's salt. So let's arrange the hash in hashcat format $ID$SALT$DIGEST. This is the format hashcat will understand while breaking the calculating the hash based on algorithm and cost factor
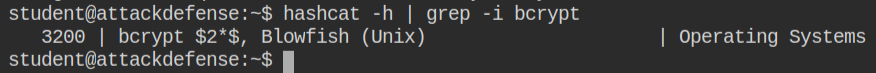
From the hashcat help message or the example page, you can get the identifier of the hash which will tell the program to use the particular hashing algorithm. As you can see the ID of the bcrypt hash is 3200, we have to pass it to -m argument in the hashcat
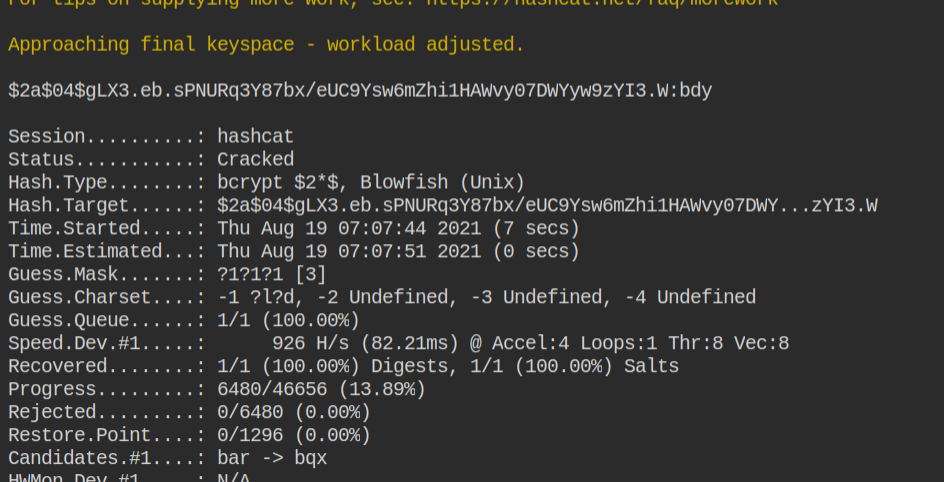
Executing the following command, didn't crack the password, which means the password plain text of the password doesn't exist in the wordlist and it is common nowadays.
hashcat -a 0 -m 3200 digest.txt 1000000-password-seclists.txtFrom the lab description, we can find a hint regarding failed dictionary attack. Also, there is a password policy as follows.
- Password length is less than 6 characters i.e. 0 < length < 4
- Password can only contain characters from this character set: a-z, 0-9
The policy is not much complicity, it's worth giving a short. We can use the mask attack mode in the hashcat which will take the charset and placeholder instead of wordlist this time. The hashcat will then generate the wordlist on the go for use and try to match the hash of the current word with the hash that has been loaded. To specify brute-force attack, you need to set the value of -a parameter to 3 and pass a new argument, -1 followed by charset and the placeholder
hashcat -a 3 -m 3200 digest.txt -1 ?l?d ?1?1?1The hashcat has basic English (ASCII) charset built-in for use and are documented here – https://hashcat.net/wiki/doku.php?id=mask_attack#built-in_charsets. However, you can provide your charset if needed.
You can see I have used -1 and ?1 placeholder. There are 4 different types of charsets that can be passed to it for a single attack and the identifiers are shown below. You can select the placeholder based on the id of the charset configured.
-1, --custom-charset1 | CS | User-defined charset ?1 | -1 ?l?d?u
-2, --custom-charset2 | CS | User-defined charset ?2 | -2 ?l?d?s
-3, --custom-charset3 | CS | User-defined charset ?3 |
-4, --custom-charset4 | CS | User-defined charset ?4 |Since the cost factor is 4, you have to wait for some time to get the cracked password in plain text